Topics List
Important Links
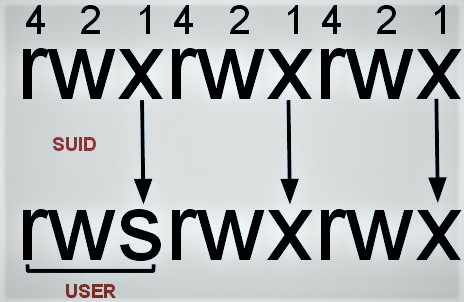
- iOS Pentesting Lab Setup with Palera1n
- WEBSOCKETS-Everything You Need To Know About W3bsock3t Pentesting!!
- A Guide to Directory Traversal Vulnerability in 2023
- The Only Information Disclosure Guide You’ll Ever Need!!
- The A – Z Of SQL Injection P3NTESTING
- SPRING BOOT PENTESTING PART 5- SECURING SPRING WEB APPS AND API
- SPRING BOOT PENTESTING PART 4- SPRING4SHELL + JOLOKIA
- SPRING BOOT PENTESTING PART 3- LAB SETUP+EXPLOITS WALKTHROUGH
- SPRING BOOT PENTESTING PART 2- ACTUATORS
- SPRING BOOT PENTESTING PART 1- FUNDAMENTALS
- TOP 40 Protocols
- WORKING OF THE WEB
- Headers And IP Message Formats
- OverTheWire Bandit 1 To 15 Full Write-up
- BurpSuite Project Options for Pentesters (PART-9)
Archives
- October 2023
- July 2023
- June 2023
- May 2023
- April 2023
- March 2023
- February 2023
- January 2023
- November 2022
- October 2021
- August 2021
- July 2021
- May 2021
- March 2021
- February 2021
- January 2021
- December 2020
- November 2020
- August 2020
- July 2020
- June 2020
- May 2020
- March 2020
- February 2020
- January 2020
- December 2019
- November 2019
- October 2019
- September 2019
- May 2019
- April 2019
- March 2019
Certcube labs YOUTUBE – lATEST UpDATES
detailed updates on mail !
Categories
- AD exploitation & Post exploitation (11)
- All Blog (71)
- buffer overflow (11)
- cloud Security (2)
- IoT pentesting (6)
- Linux privilege escalation (14)
- mobile application security (9)
- OSCP Study material (34)
- web application pentesting (9)
- Windows-Pentesting (12)






Recent Comments