The Anatomy of the iOS file system in Depth -101
This blog gives a detailed understanding of the file system of an iPhone. In order to completely understand the environment of an iOS application, it is crucial to comprehend the file system in which iOS application components and data reside.
Choosing a preferable means to enter the iOS file system
You can enter the iOS file system using three methods as discussed in the previous article. The three ways are:
- Using a GUI-built application (such as Filza File Manager) on the iPhone.
- using the root ID and password in the iPhone
The root directory (‘/’)
By using the aforementioned methods, you can enter the file system and observe the files and directories in it. We will first observe the starting point of the file system i.e. ‘/’ also called the root directory. The contents of ‘/’ in iOS as shown in the below screenshot.

Some of the key highlights are:
- In a jailbroken device, all the files and directories under ‘/’ have read and write access.
- The directories directly found under ‘/’ can be categorized according to their name as follows:
- Directories are similar to macOS file systems: Applications, Library, System, User.
- Directories are common to UNIX file system: bin, boot, dev, etc, lib, mnt, sbin, tmp, usr, var.
- Directories are unique to the iOS file system: private, cores.
- Other directories depend on the jailbreaking tool used.
- Some of the directories are symlinks to other directories under the ‘/’.
- The symlinks usually point to some directory that comes directly or indirectly under the /private directory.
- There may be also a file with the name ‘.file’. It appears to have no purpose, but it may be used for file integrity checks to verify the filesystem is not corrupt.
The root user’s home directory ‘/var/root’ -> /private/var/root
The default directory you land up in when you access the iOS file system through the command line is ‘/var/root’. This directory is a symlink to the path /private/var/root. It is called the home directory of the root user running the command ‘cd ~’ through the command line as the root user will get you to this particular directory.

The important observations to be noted for the files and folders under this directory are:
- It contains two directories by default — Application Support and Library
- The /var/root directory is the root directory of the ‘root’ user.
The directories in the PATH
By default, the PATH variable holds the directories /bin, /sbin, /usr/bin, /usr/sbin. All these directories hold various essential binaries for the iOS file system.

The iOS Application Environment
An iOS application has access to the following directories/components to exchange data from:
Pre-installed Native iOS Application and Native Jailbreak Application Directory
/Applications/$app_name.app
App Store Application Directory
/var/containers/Bundle/Application/$uuid
Data Directory
/var/mobile/Containers/Data/Application/$uuid
Shared Data Directory
/var/mobile/Containers/Shared/AppGroup/$uuid
iOS Keychain
/var/Keychains/keychain-2.db
UIPasteboard
Clipboard of iPhone
Pre-installed Native iOS Application Directory
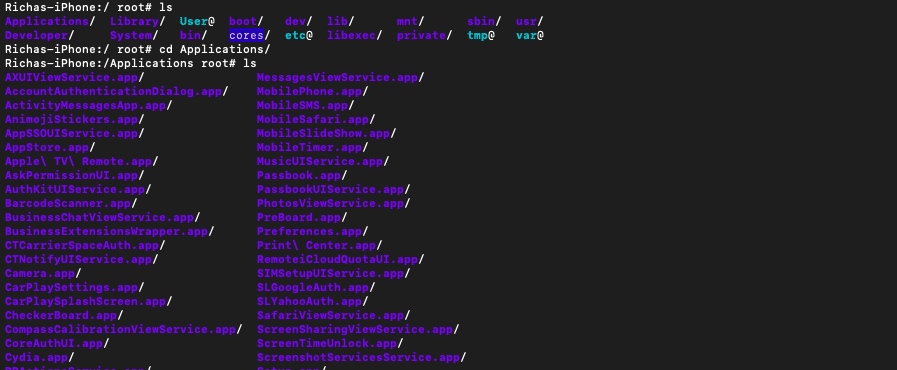
- This directory stores the pre-installed iOS applications and the native jailbreak applications.
- The path to this directory is /Applications/{app_name}.app where app_name is the name of the application.
- They can’t be deleted under normal circumstances.
Note: Deleting the application directories is not recommended because they cannot be reinstalled once deleted
App Store Application Directory
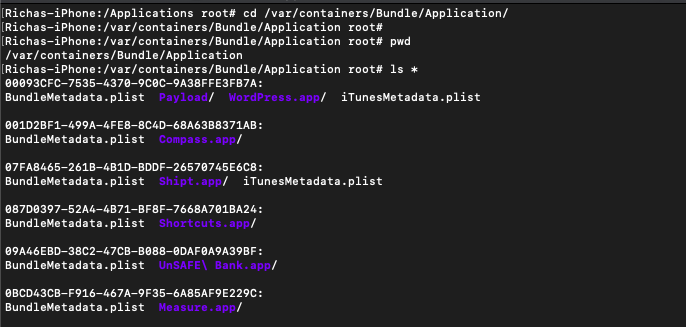
- This directory stores iOS applications that you install from the App Store like games, tools, photo/video editors, etc.
- The path to this directory is: /var/containers/Bundle/Application/{uuid} where uuid is the UUID of an application. UUID is unique for each application and always changes for a fresh installation of that application.
- The files inside the directory of a particular application together make what is actually the IPA file of that application.
Analyze the plist file – plistutil –
install it with – apt-get install libpist-utils
syntex – plistutil -i Info.plist -o Info_xml.plist
Data Directory
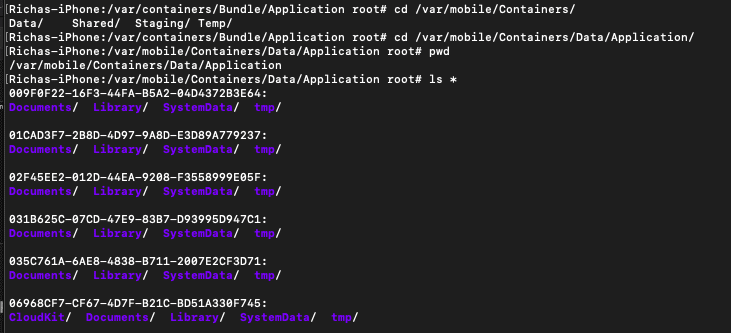
- This directory stores the local data of all the applications.
- The path to the data directory is: /var/mobile/Containers/Data/Application/{uuid} where UUID is the UUID of an application. UUID is unique for each application and always changes for a fresh installation of that application.
- The files inside the directory of an application contain the local data storage of the application and can be accessed only by that particular application on a non-jailbroken device due to the sandboxing provided by iOS.
Shared Data Directory
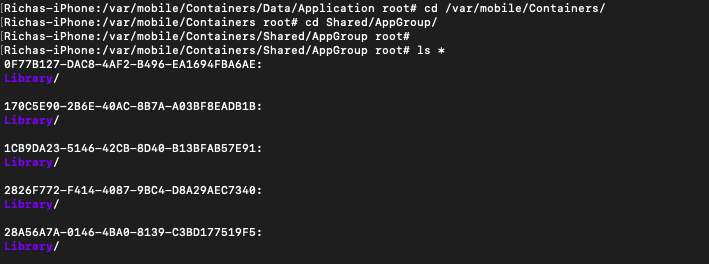
- This directory stores the data shared by a group of applications or their own extensions.
- The path to the data directory is: /var/mobile/Containers/Shared/AppGroup/{uuid} where uuid is the UUID of the application group.
- All the installed applications may not have an entry in the Shared Data Directory.
iOS Keychain
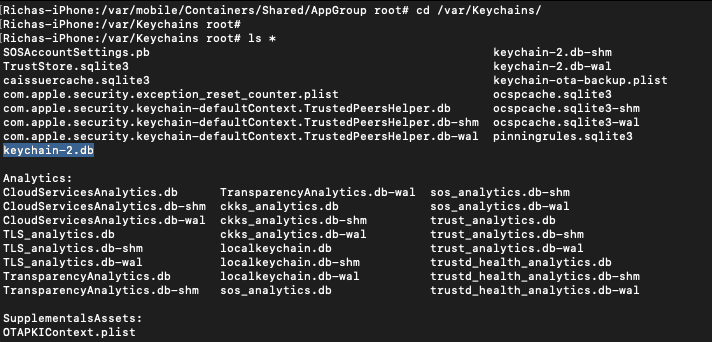
- It is an SQLite database file that contains the items stored by the iOS keychain for any application including the WiFi passwords, iTunes Apple ID, etc.
- The file resides under the directory /var/Keychains/
- The name of the file is keychain-2.db
- The file consists of all the keychain entries in encrypted form.
UIPasteboard
- It contains the text including special characters like emojis that are copied from a text source such as a website or a document.
- It can be accessed by using Cycript, FRIDA, etc.
holy shit! So the file system architecture was briefly explained in order to know the environment in which an iOS application resides and works. We now have a better approach to the environment of an iOS application
Learn Advanced IOS Exploitation and Security with our brand new Training – Click Me
Recent Comments