iOS IPA Architecture for Pentesters
iOS application security is the most trending topic nowadays on social media. Although Apple claims that they are building the best products in the market in terms of manufacturing the CHIP, iPhone Hardware to Apps task handling is based on AES 256 encryptions and Apple focuses a lot on consumers’ personal data security. I am not going into the details of iPhone Architecture in this blog. We will focus on iOS apps and the iOS IPA architecture from a pentester point of view.
There are three types of iOS applications:
- Native applications use Objective C/Swift to build the application
- Hybrid applications use frameworks like Xamarin, Cordova, etc. along with Objective C/Swift.
- Web-based applications are responsive versions of websites built for working on mobile devices.
We would be currently focusing on native iOS applications. A native iOS application can use Objective C or Swift code along with any of its native libraries or frameworks available for use in iOS applications.
So let’s divide the Application architecture into Some chunks: –
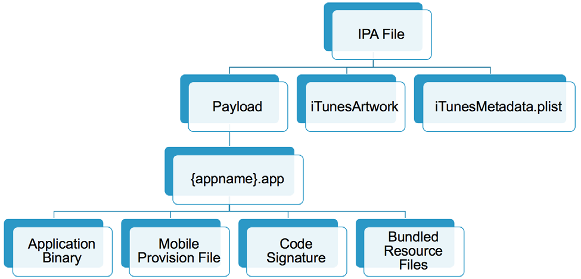
iOS apps are distributed in IPA (iOS App Store Package) archives. The IPA file is a ZIP-compressed archive that contains all the code and resources required to execute the app.IPA files have a built-in directory structure.
- /Payload/ folder contains all the application data. We will come back to the contents of this folder in more detail.
- /Payload/Application.app contains the application data itself (ARM-compiled code) and associated static resources.
- /iTunesArtwork is a 512×512 pixel PNG image used as the application’s icon.
- /iTunesMetadata.plist contains various bits of information, including the developer’s name and ID, the bundle identifier, copyright information, genre, the name of the app, release date, purchase date, etc.
- /WatchKitSupport/WK is an example of an extension bundle. This specific bundle contains the extension delegate and the controllers for managing the interfaces and responding to user interactions on an Apple Watch. For example the AWS SDK.
/Payload Folder In Detail
Let’s take a closer look at the different files in the IPA container. Apple uses a flat structure with few extraneous directories to save disk space and simplify file access. The top-level bundle directory contains the application’s executable file and all the resources the application uses (for example, the application icon, other images, and localized content.
- MyApp: The executable file containing the compiled (unreadable) application source code.
- Application: Application icons.
- Info.plist: Configuration information, such as bundle ID, version number, and application display name. It can be viewed with a text editor. If it is in a binary format, can be converted using
- Launch images: Images showing the initial application interface in a specific orientation. The system uses one of the provided launch images as a temporary background until the application is fully loaded.
- MainWindow.nib: Default interface objects that are loaded when the application is launched. Other interface objects are then either loaded from other nib files or created programmatically by the application.
- Settings. bundle: Application-specific preferences to be displayed in the Settings app.
- Custom resource files: Non-localized resources are placed in the top-level directory and localized resources are placed in language-specific subdirectories of the application bundle. Resources include nib files, images, sound files, configuration files, strings files, and any other custom data files the application uses.
on a jailbroken device you can install the IPA file with IPA Installer, iFunbox, Cydia impactor, or intallipa command inside in the rooted phone.
During mobile security assessments, developers often give you the IPA directly. They can send you the actual file or provide access to the development-specific distribution platform they use, e.g., HockeyApp or TestFlight.
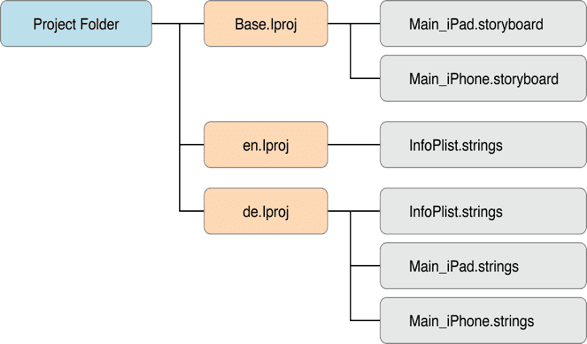
A language.lproj folder exists for each language that the application supports. It contains a storyboard and a strings file.
A storyboard is a visual representation of the iOS application’s user interface. It shows screens and the connections between those screens.
The strings file format consists of one or more key-value pairs and optional comments.
On a jailbroken device, you can recover the IPA for an installed iOS app using various tools like frida-ios-dump , iNalayzer etc that allow decrypting the main app binary and reconstructing the IPA file.
That’s all about this blog in the next blog we will understand How to extract the IPA from the device and How you can analyze the IPA with various methods.
Learn IOS Exploitation and Security Pentesting with our most advanced IOS Security Course- Course Link


Recent Comments