Android Pentesting Lab Setup – 101
HEY FOLKS!!!
Let’s Talk About Android PenTesting Lab Setup!!!
Mobile or Android penetration testing is a security assessment process that looks for vulnerabilities in mobile applications and makes sure they are not vulnerable to attacks.
An Android mobile penetration tester can use automated or manual methods to analyze an application for security vulnerabilities. This can include simulating attacks, finding security flaws, and gaining access to sensitive data.
Why Android PenTesting Is Important!!
Android applications are used in a variety of commercial and non-commercial applications. They can be used for security purposes, as they often contain vulnerabilities. Penetration testers and developers use these vulnerabilities to find and fix them, which helps to protect the company’s data and avoids security risks.
By fixing these vulnerabilities, companies can mitigate security risks and go live with new apps without worrying about legal or security issues.
Mobile penetration testing can help evaluate the quality of an app’s development team and the responsiveness of the IT team, as well as find vulnerabilities in back-end services used by the app.
Also, they can help evaluate the work of the app’s developer team and the responsiveness of the IT team to app-related issues.
Tools For Android PenTesting!!
There are a variety of tools available for penetration testing Android applications. Some are automated, while others are done manually.
Android penetration testing tools can help find common vulnerabilities on Android devices, which can be faster and cheaper than using manual methods. Some of them are listed below.
- Burp Suite -A proxy-based tool used to perform manual tests by capturing and tampering request/response. Also, this is a tool for web application pen-testing.
- Ghidra – It is an excellent reverse engineering tool and unlike Ida Pro, it’s free! Ghidra has nearly all the functionality of Ida Pro without the cost, so if you are starting out in reverse engineering, this is probably the software to use.
- Zed Attack Proxy (ZAP)–It is an alternative tool for burp suite and has somewhere similar features.
- Drozer– Drozer is a powerful Android application security testing framework that makes it easy for testers to create test cases and check for vulnerabilities in the components of an application. It has been praised by leading mobile application security testing books and is the de-facto standard for Android application security testing.
- Fiddler– The Fiddler tool helps you debug web applications by capturing network traffic between the Internet and test computers.
- Frida– This toolkit is designed to help developers, Reverse Engineers, and Security Researchers analyze and debug code, and improve their security skills.
- MobSF– Mobile Security Framework is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment.
- Android Debug Bridge (ADB)– A versatile command-line tool that lets you communicate with a device and pentest with the machine.
Let’s Set-up The Android Pen-Testing Environment
Pre-requisite:
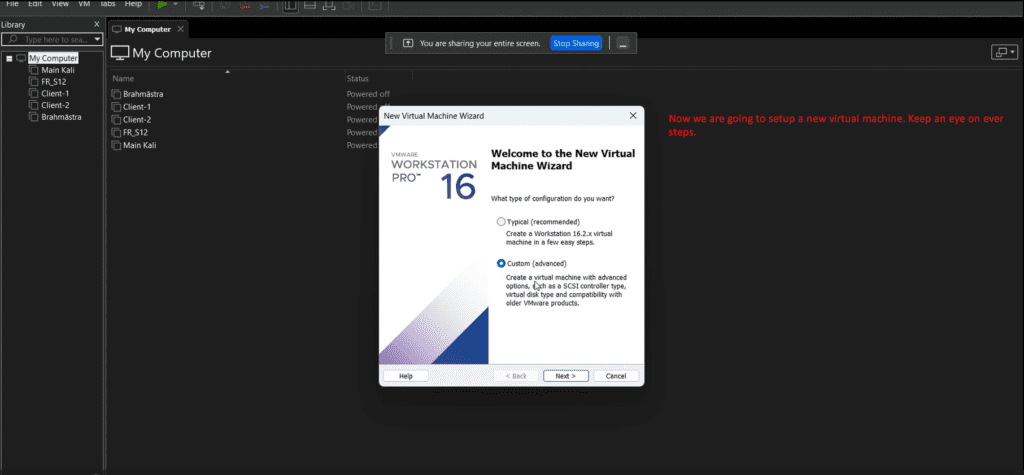
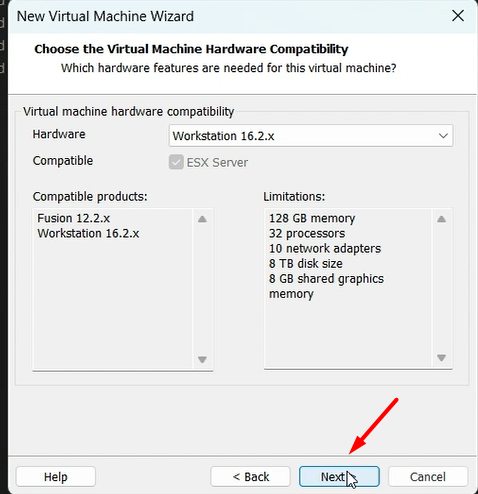
- VMware Workstation
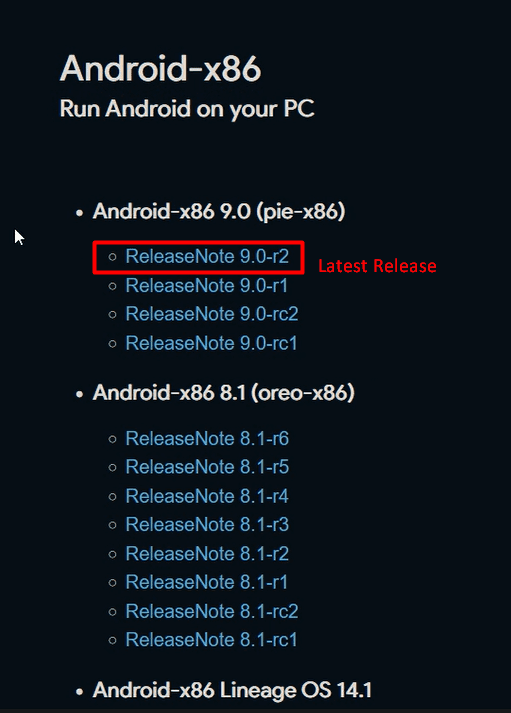
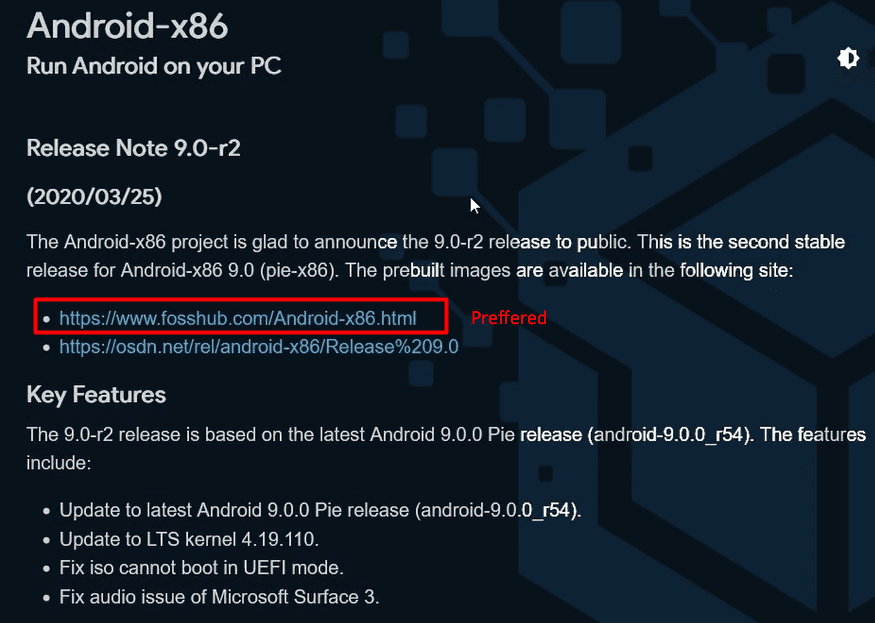
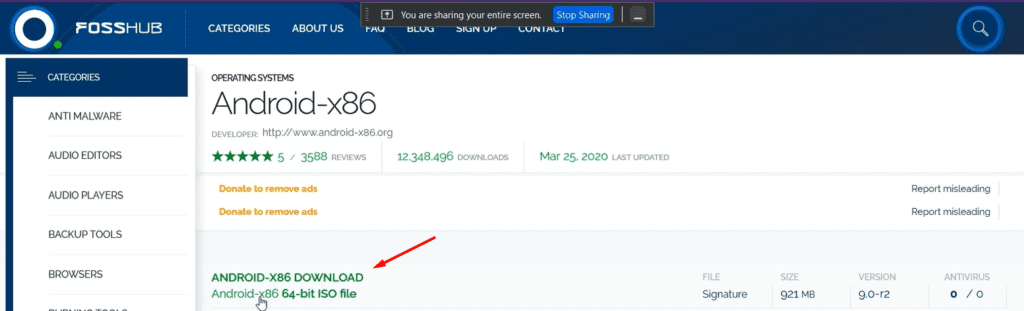
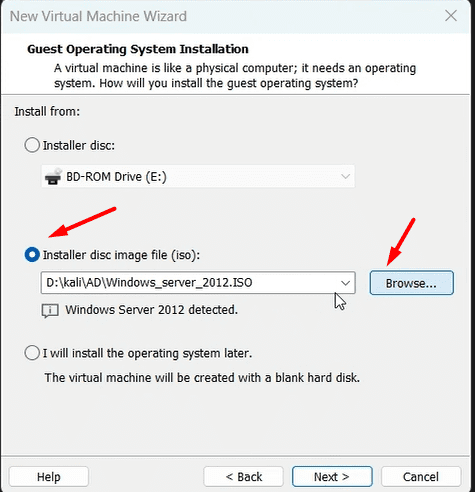
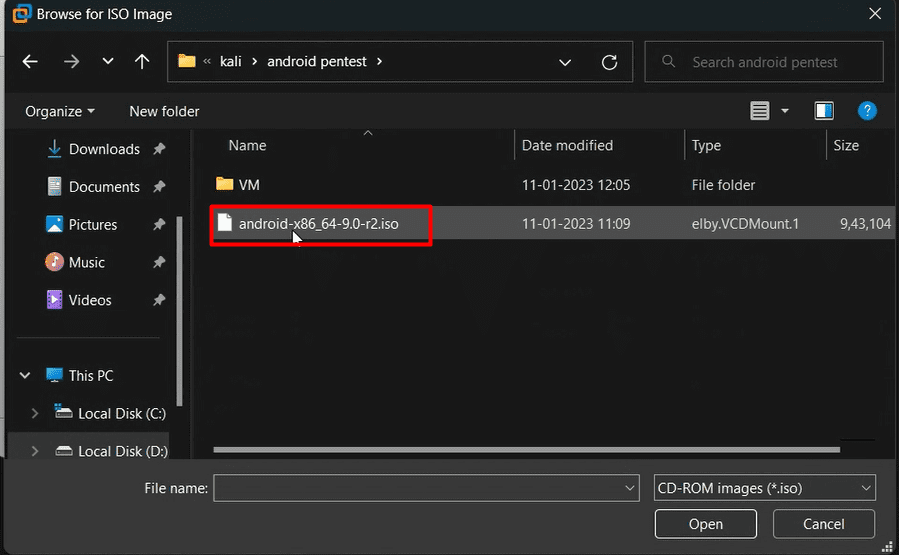
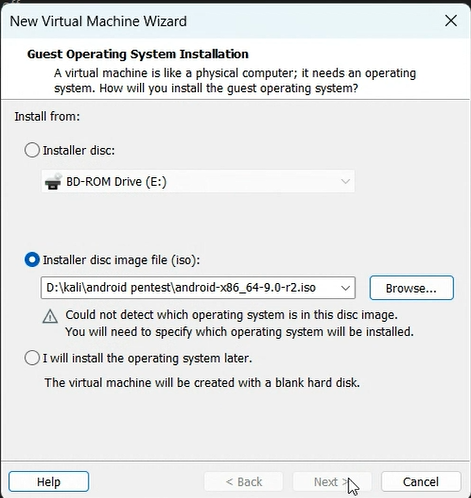
- Android-x86– Android-x86 is an unofficial porting of the Android mobile operating system developed by the Open Handset Alliance to run on devices powered by x86 processors.
Now let’s begin with the setup:-
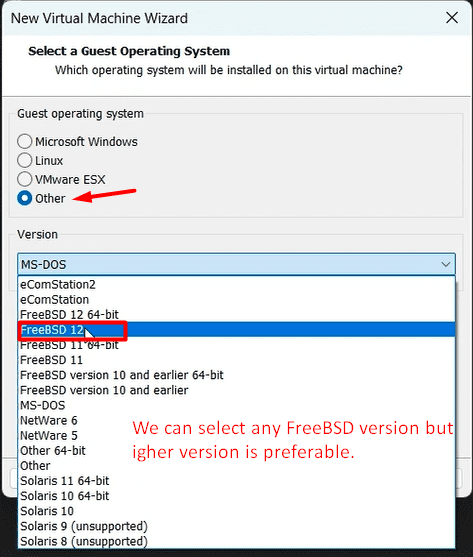
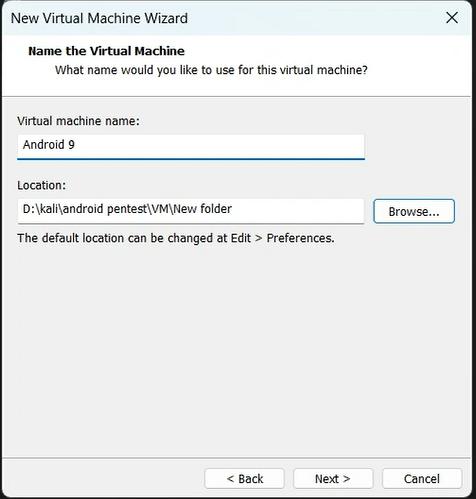
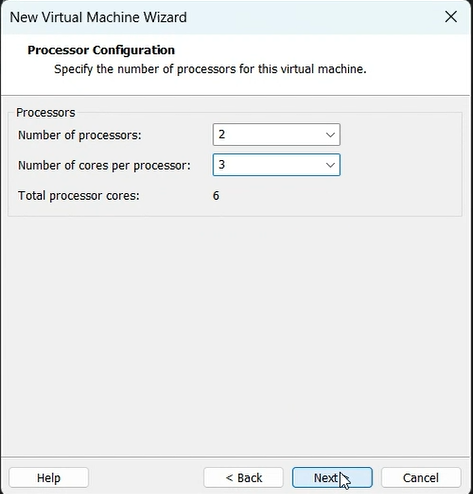
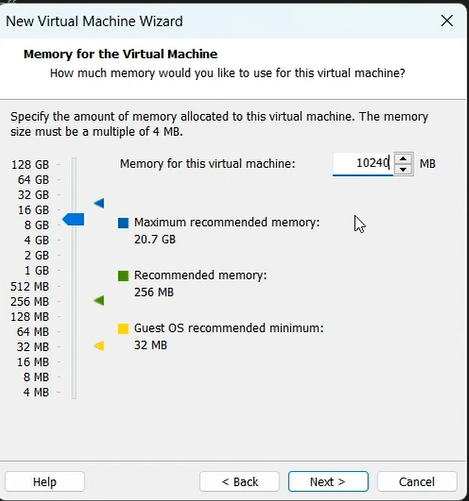
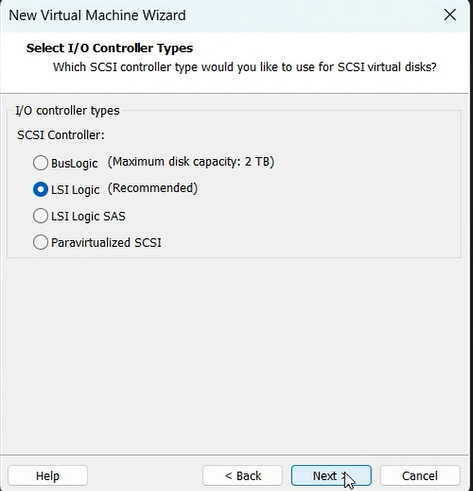
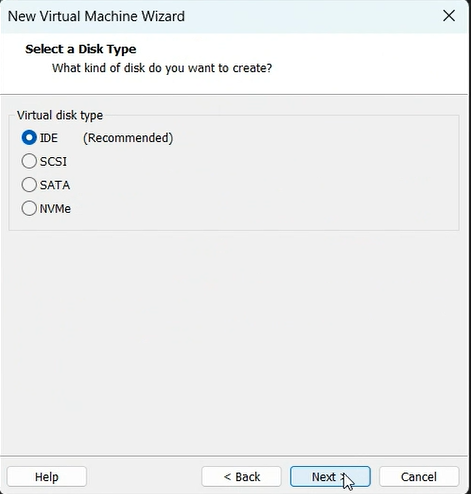
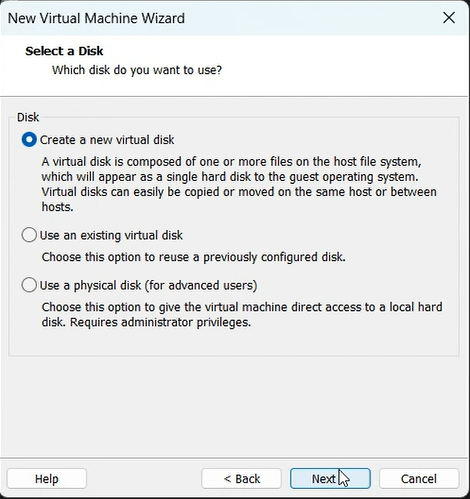
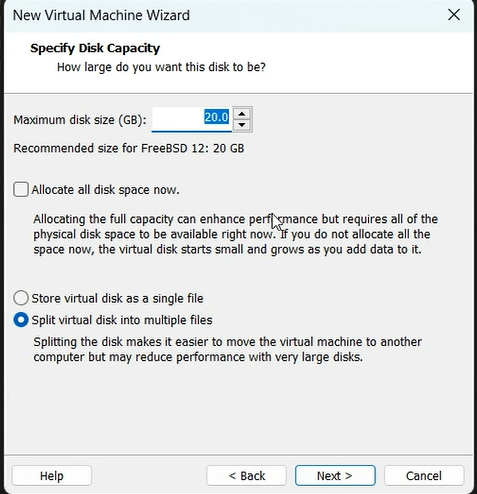
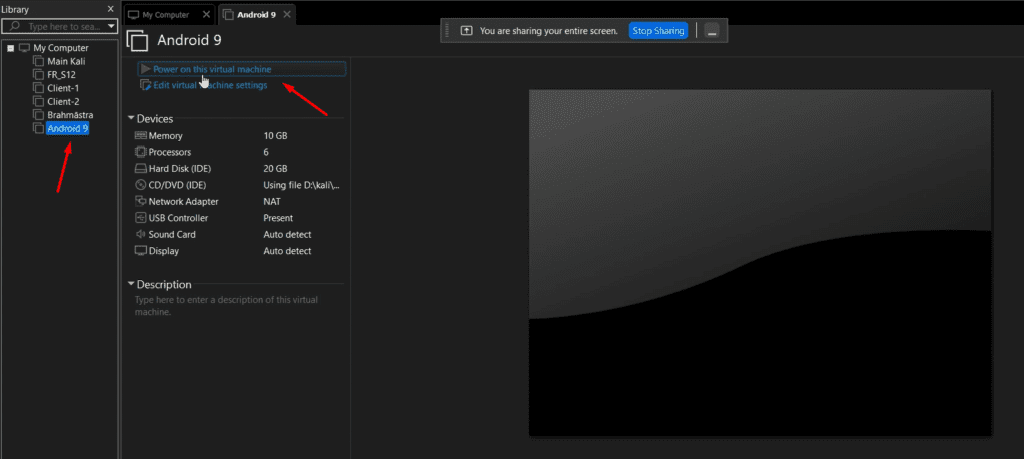
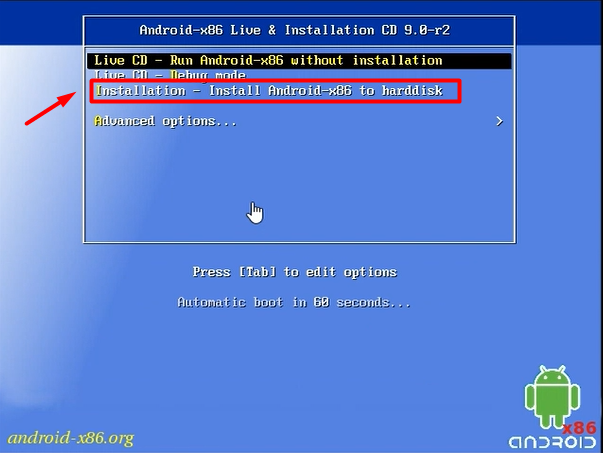
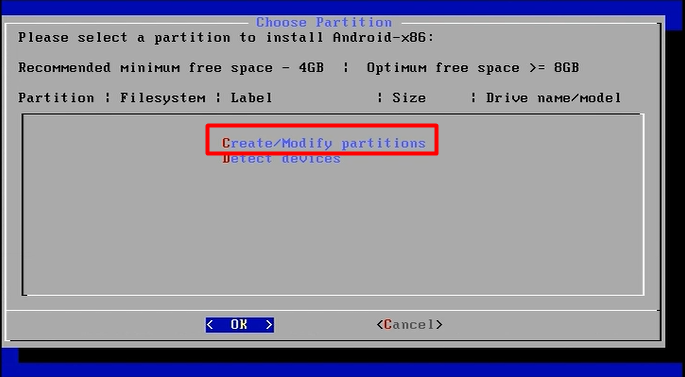
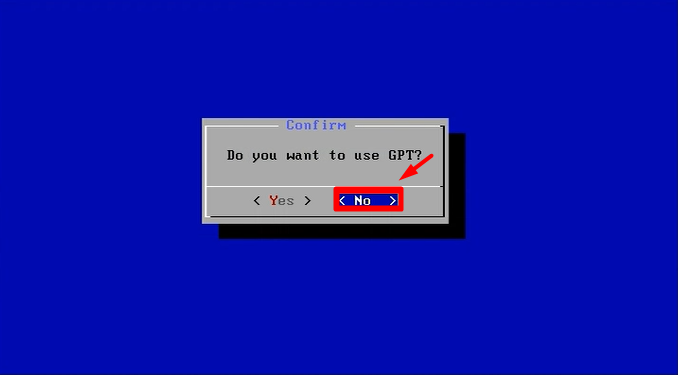
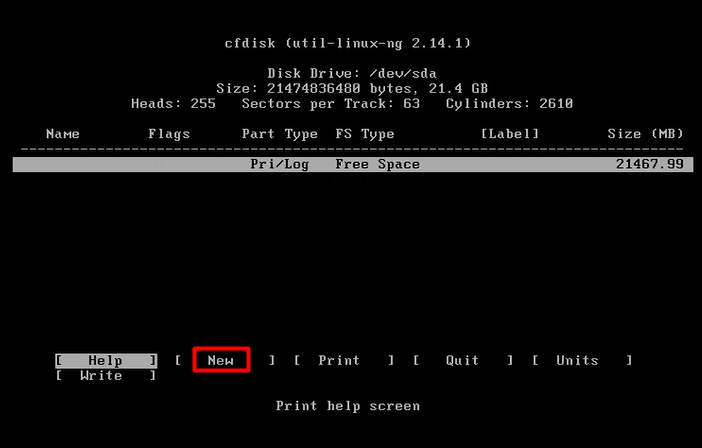
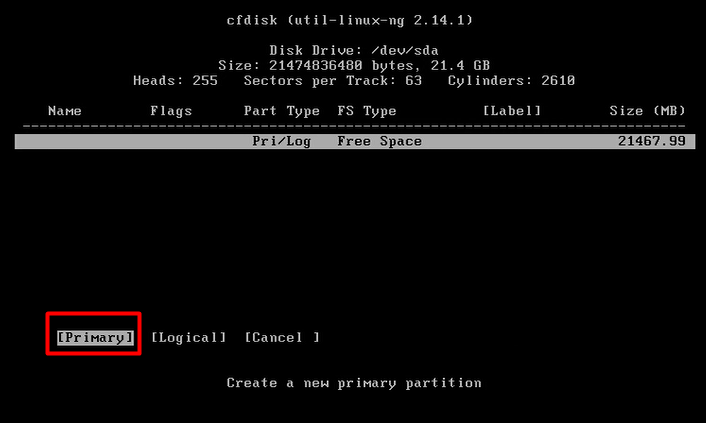
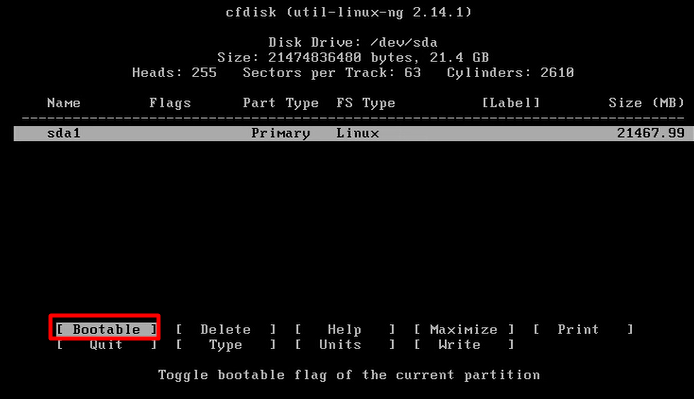
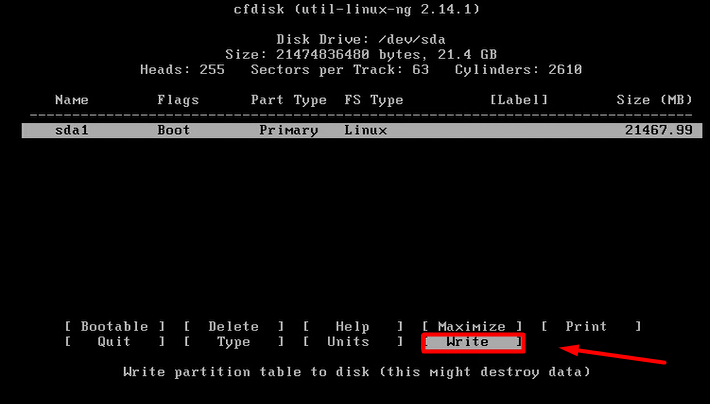
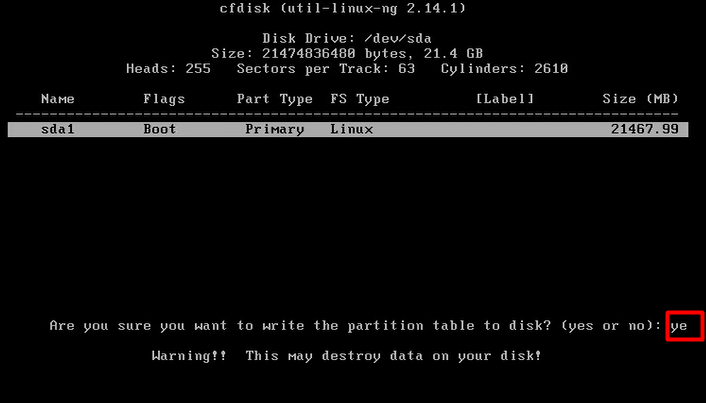
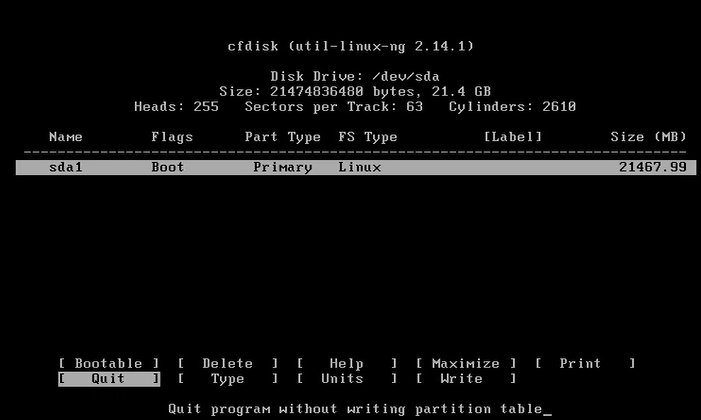
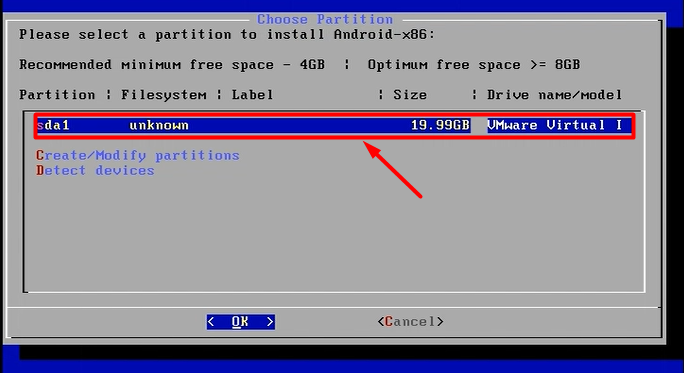
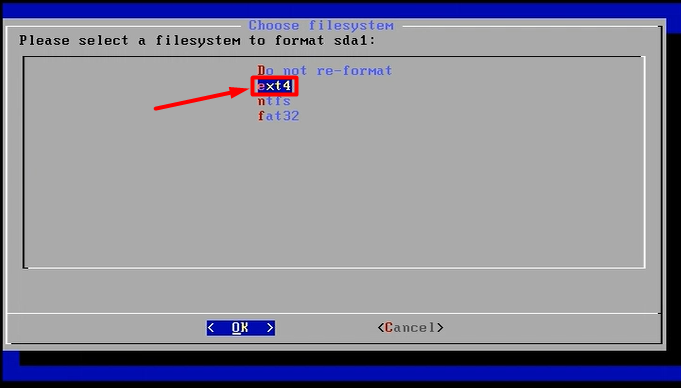
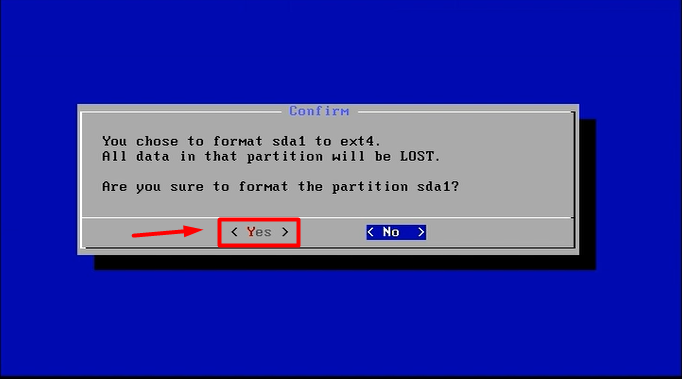
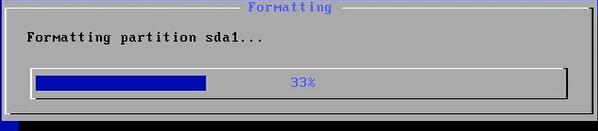
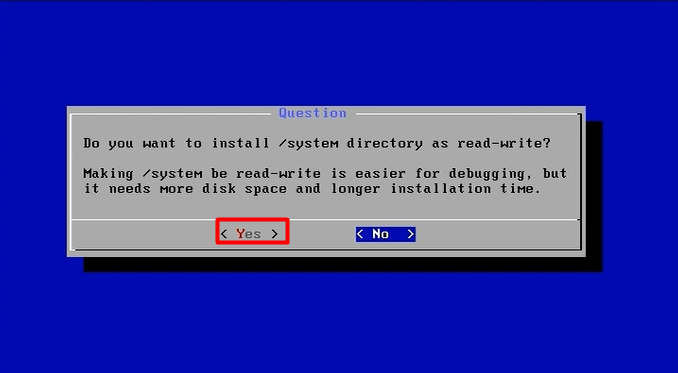
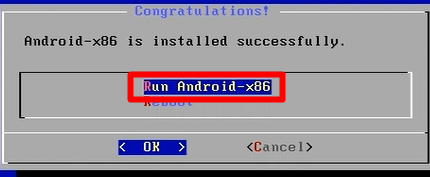
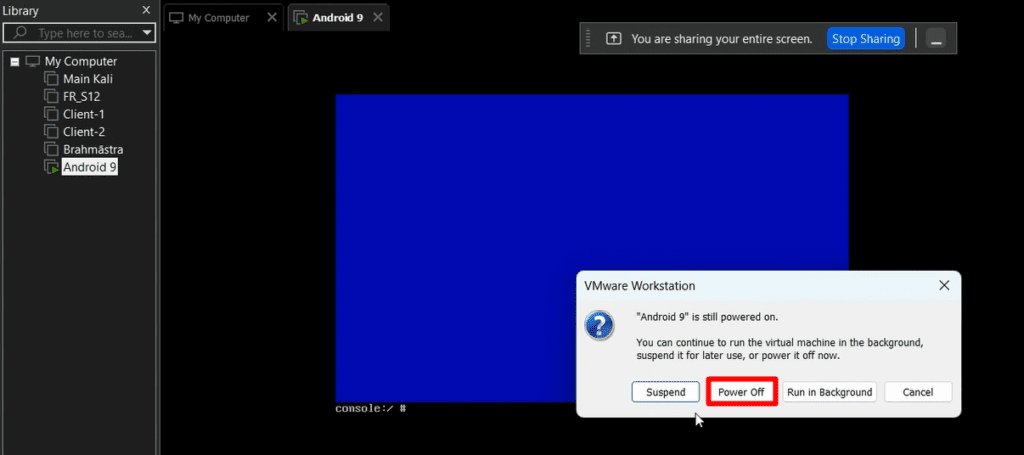
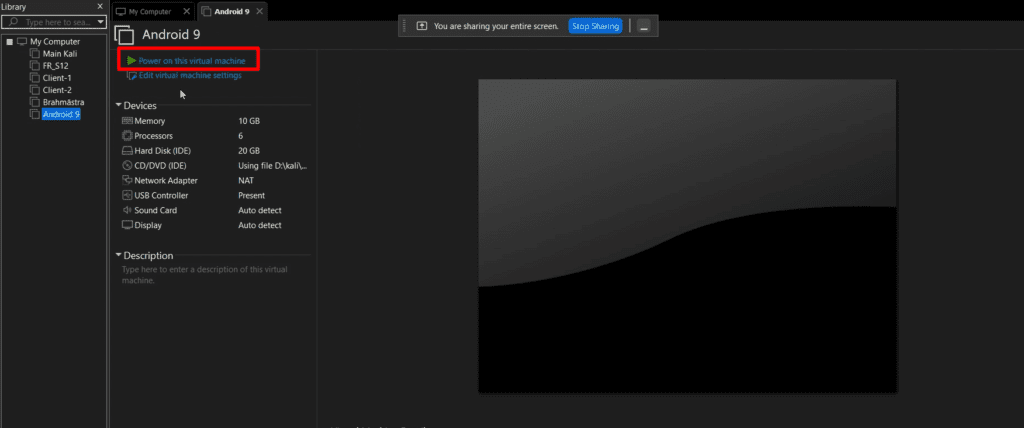
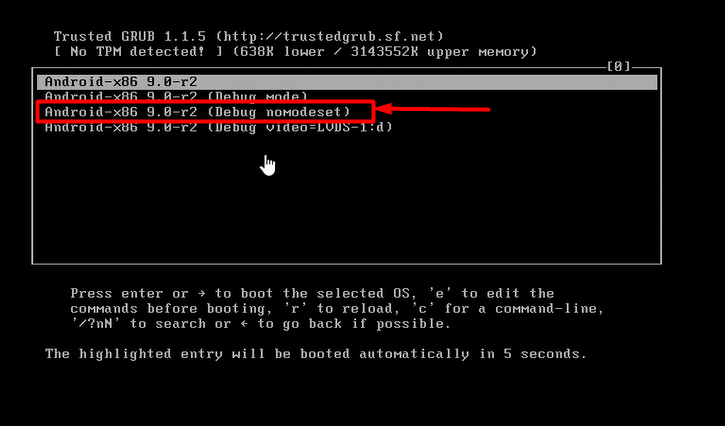
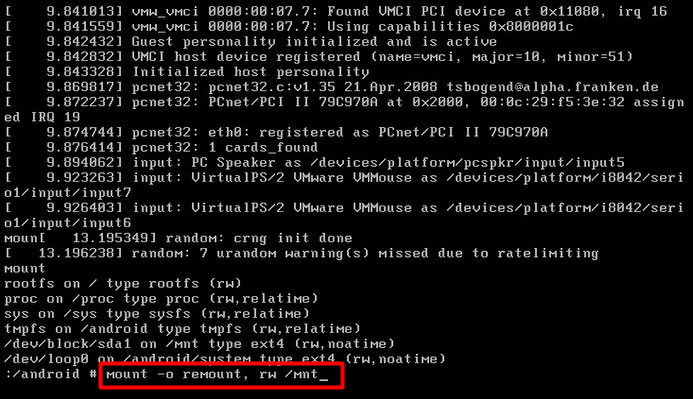
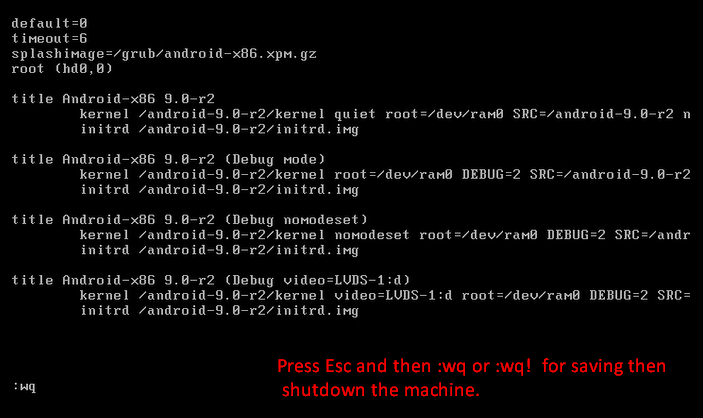
mount -o remount, rw /mnt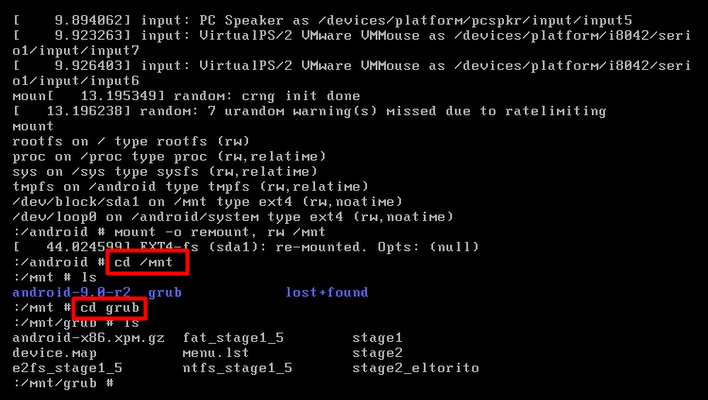
cd /mnt
ls
cd grub
ls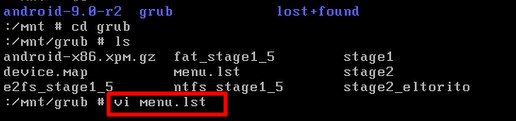
vi menu.lst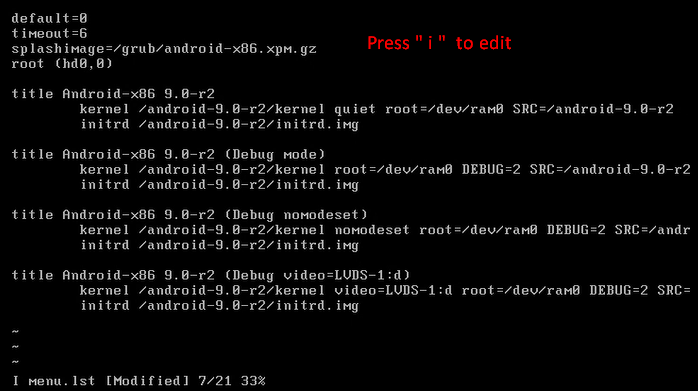
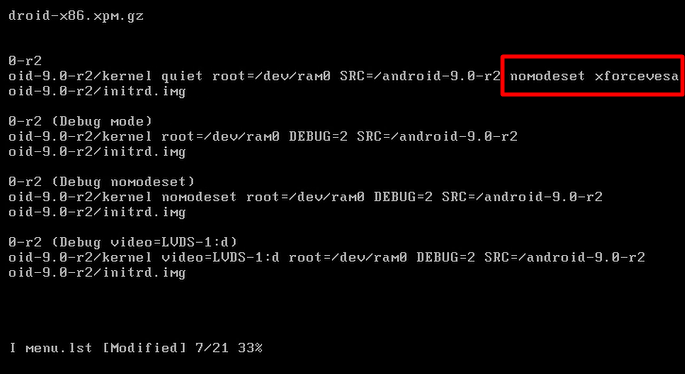
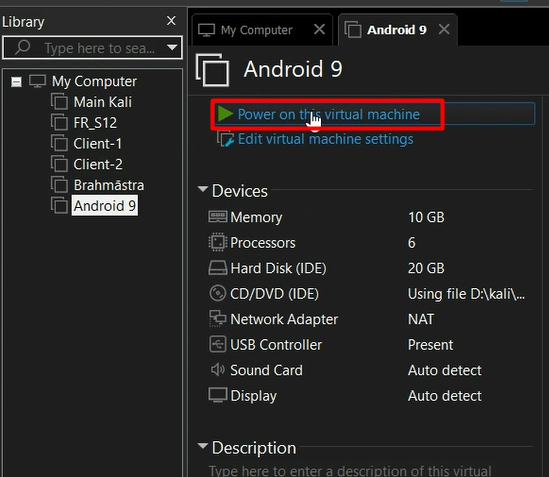
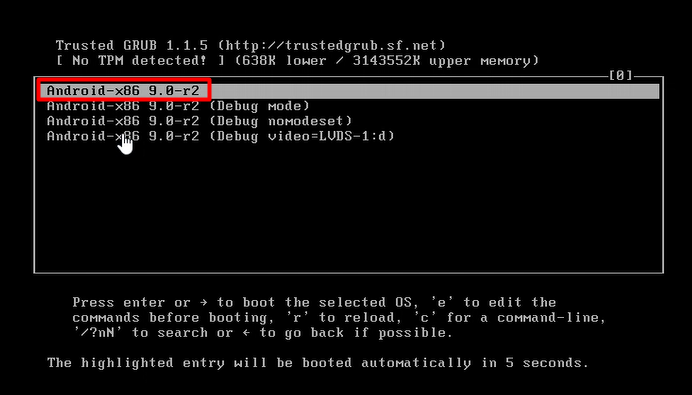

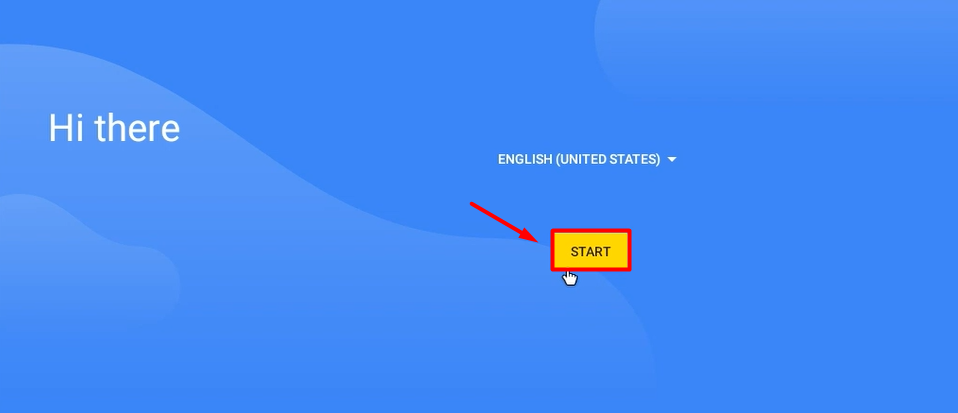
To understand in a better way, there’s a video provided below on Android pentesting lab setup for your ease.
Thanks for visiting this blog!!!
Recent Comments