The Only Information Disclosure Guide You’ll Ever Need!!
Information Disclosure? Let’s Talk About It!!
Information disclosure, generally occurs when a website unintentionally reveals sensitive information to its users. This could include everything from personal details to confidential information. Depending on the context, this information could be easily accessed by an attacker, potentially leading to serious security risks.
This is information about other people, such as their usernames or financial information. This could also include sensitive information about businesses or the website’s infrastructure.
Leaking sensitive user or business data can be risky, but disclosing technical information can be just as damaging. By knowing what’s out there, attackers may be able to more easily exploit vulnerabilities on your system. This information could also be useful when trying to build complex attacks.
Sensitive information can be accidentally revealed to website visitors who are browsing the site casually, but more commonly, it is accessed by attackers who try to exploit the site in ways that are unexpected or malicious. After analyzing the website’s responses, they may be able to identify interesting behavior that could be used to their advantage.
Let’s Find Out How Information Disclosure Vulnerabilities Arise And Impact!!
There are many ways information disclosure vulnerabilities can occur, but these can generally be categorized into two types: accidental and intentional.
Failing to remove internal content from public content can lead to security risks. Additionally, insecure configurations of website and related technologies can allow attackers to gain access to sensitive information. Poor design and behavior of an application can also lead to vulnerabilities.
Information disclosure vulnerabilities can have different impacts depending on the purpose of the website. For example, if a website is used to sell sensitive information, disclosure of that information alone can have a big impact on the people affected.
Information that is leaked, such as the directory structure or which third-party frameworks are being used, may have little direct impact, but could be the key information needed to construct other exploits. However, if leaked information falls into the wrong hands, it could have a significant impact.
Mostly they are occurred because :-
- Bad Configuration
- Using a Poorly designed application
- Also, if fails to remove the sensitive content from public content.
Some issues / types of information disclosure!!
- Banner Grabbing
- Source Code disclosure
- File name and file path disclosure
- Backup Files
- Credentials
- API key, Secret key (Private key & Tokens)
Common Ways to find the Information Disclosure
- This technique involves listing the subdomains and then utilizing a desirable word list to scan the endpoint. Tools like dirsearch and ffuf can be employed to execute this process. To be effective, it’s important to use the right word list. You can use Asset note Word lists or six2dez/OneListForAll: Rockyou for web fuzzing (GitHub.com) for fuzzing. This approach allows you to not only discover instances where sensitive information is being exposed, but also enables you to identify additional ways to search for different vulnerabilities, such as finding hidden pages and parameters.
- The Common sources of information disclosure are :-
- In view Source we got disclosed information.
- Sometimes robots.txt, phpinfo.php will disclose information.
- Sometime SQL error mentioning database or column names
- File name file path disclosure information.
- Thumbnails reveals sensitive information.
- Run time error generated by server.
- Must visit robots.txt and sitemap.xml, they are basically provided by the websites to help the crawlers navigate to the site. If they are not detected in burp then it recommended to manually visit and might we can find anything of use.
- Unencrypted Cookie parameters or view state disclosed sensitive information.
- Mostly the servers are configured in a way that the contents of directories that do not have index page present, and we can directly identify the resource at the path we can use direct payloads with ffuf or dirsearch.
- During development, in-line HTML comments are added to the markup. So they are stripped before changes and can be forgotten, missed or even left in deliberately as someone is not aware of security functions Example -might hint at the existence of hidden directories or provide clues about the application logic.
- Always ready to use the Burps’ engagement tools and search, Find comments and discover content.
- Verbose error messages can also provide information about different technologies being used by the website. For example, they might explicitly name a template engine, database type, or server that the website is using, along with its version number. This information can be useful because you can easily search for any documented exploits that may exist for this version. Similarly, you can check whether there are any common configuration errors or dangerous default settings that you may be able to exploit.
- So in addition found out that TRACE is used to bypass which can reveal the information, not that much but can be useful as it can reveal the header name which is new we can use the header in every request by using the Proxies option, and then we go to proxies, in match and replace we use the replacement only with the 127.0.0.1(with the header) and hence we got access to the admin panel.
- For the disclosure part, some information can be stored in .git folder and can be accessed via /.git and can be discovered in content discovery. So (/. Git) can be downloaded via wget command, and then it’s a .git a hidden file, so now we all have to do is use ls -a to list the hidden .git file and then access it using Git Cola.
- Basically in the above all we have to do is download the .git within a new folder with “wget -r URL” and after this we have to open it using the git cola then we have to use undo last commit.

TOOLS with usage
- Assetfinder- It is used in subdomain enumeration.Finds domains and subdomains potentially related to a given domain.
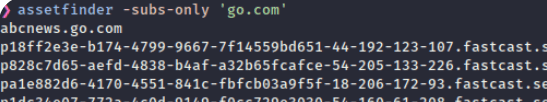
Command- assetfinder -subs-only example.com
- Wappalyzer-It identifies technologies on websites, such as CMS, web frameworks, ecommerce platforms, JavaScript libraries, analytics tools. It can be installed though add-ons on chrome and Firefox and identifies technologies.
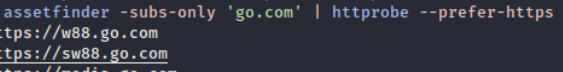
- httpProbe-Take a list of domains and probe for working http and https servers.The httprobe tool serves the purpose of verifying the presence of an HTTP service on a domain. It has a default setting that checks the 80 and 443 ports, but can be configured to include additional ports using the -p flag. I personally like to use it with assetfinder tool. I directly pipe the output of the assertfinder to the httprobe.
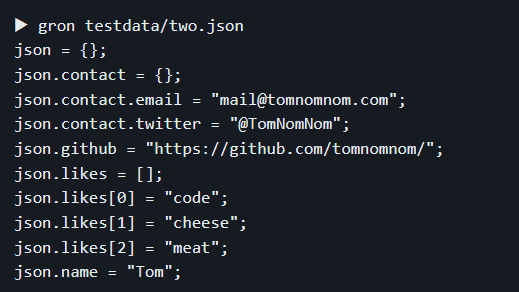
- gron-is a tool that allows for more efficient searching of JSON output. It can extract the value of a specific key and has colored output. Additionally, it has the capability to save and convert the output back to JSON. Furthermore, Gron can also function as an HTTP client.
- meg-Meg is a valuable tool for enumeration. It allows us to request endpoints from multiple hosts, which can be specified in a file. The results from each host can be stored in separate directories. Additional options for using Meg can be found by using the –help flag. To use Meg, simply place the hosts in a file called “hosts” and the paths in a file called “paths”, and then run the command.
- waybackurl-If your dirbuster or gobuster tool is not sufficient for finding hidden files and directories on a target, you can use a tool that uses the webarcv website to discover more endpoints on the internet.
- Naabu-(I prefer nmap)Naabu is a powerful and efficient port scanning tool developed in the Go programming language. Its primary function is to assist in identifying valid ports for hosts with remarkable speed and reliability. This tool, although simplistic in design, executes rapid SYN/CONNECT/UDP scans on a single host or a list of hosts, subsequently providing a comprehensive list of ports that elicit a response.
- Usage- naabu -h (This will display help for the tool. Here are all the switches it supports.)
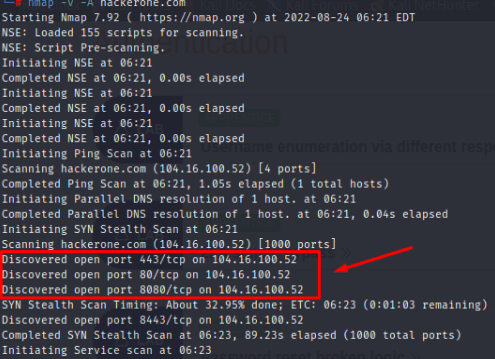
- Example- naabu -p 80,443,21-23,u:53 -host hackerone.com
- By default, the Naabu checks for nmap’s
Top 100ports. - Now naabu has nmap integration support .
- To use,
nmap-cliflag can be used followed by nmap command. - For example:-echo hackerone.com | naabu -nmap-cli ‘nmap -sV -oX nmap-output’
subfinder-: Subfinder is a tool that helps discover subdomains for websites by utilizing passive online sources. Its architecture is straightforward and can function at high speeds. Subfinder’s primary focus is on passive subdomain enumeration, and it excels in that area.- Usage- subfinder -h
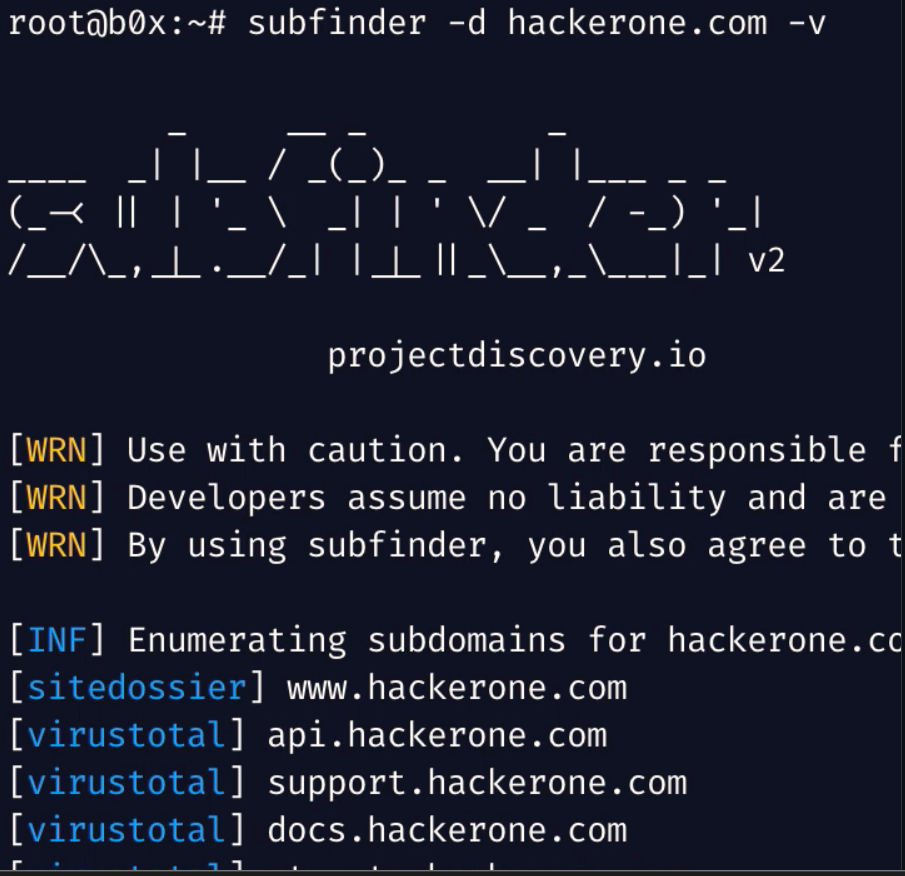
- Nuclei– is a tool that enables the sending of requests to multiple targets using a template system, resulting in a high level of accuracy and efficient scanning of numerous hosts. It supports a wide range of protocols, such as TCP, DNS, HTTP, SSL, File, Whois, Websocket, Headless, and more. Nuclei’s customizable templates allow for diverse security checks to be modeled.
- Usage- nuclei -h
- Read more here .
Let’s Talk about Prevention/Mitigation to avoid Information Disclosure
- It is important to avoid putting sensitive information such as credentials, API keys, IP addresses, and personal names directly into the code, even as comments.
- Ensure that the services operating on the server’s accessible ports do not disclose details about their constructions and editions.
- Whenever possible, use vague error messages to avoid giving attackers any unnecessary insight into how the application behaves.
- Set up the web server to prohibit displaying directories and ensure that the web application consistently displays a default page.
- The server should not display any errors on the user interface. Proper checks should be in place to catch all errors. It is recommended to create a standardized error page or log errors in a file. Avoid putting any content in HTML comments.
Refrences-:
- https://hbothra22.medium.com/recon-to-sensitive-information-disclosure-in-minutes-503fc7ccdf0b
- https://sapt.medium.com/research-on-clickjacking-network-sniffing-cyber-sapiens-internship-task-14-627e3fcb2d19
- https://allabouttesting.org/top-25-example-usage-of-ffuf-web-fuzzer/
- https://gupta-bless.medium.com/exploiting-information-disclosure-41cb1802cda0
- https://github.com/orgs/projectdiscovery/repositories?type=all
- https://technicalnavigator.in/tomnomnom-tools/
In the Next blog, we will learn about Web sockets and practice the labs!!
Read our Previous Blogs.
If you enjoyed this blog post, share it with your friends and colleagues!!
Recent Comments