Windows Privilege Escalation Methods
Windows, compared to other operating systems, holds a market share of over 80% for desktops. It is the de-facto standard operating system of enterprises and organizations for their employees’ workstations. Microsoft offers different editions of Windows. From Windows Home, Education to Enterprise; every edition has its target audience and functions.
Furthermore, there are Windows Desktop and Windows Server versions. Windows Server supports more memory, uses CPUs more efficiently, allows more network connections than Windows Desktops and is configured to prioritize background tasks (e.g. file servers, web servers, databases) while Windows Desktop prioritizes foreground applications.
Note:- Those who know basics stuff about windows OS; can skip this part and directly start reading from privilege escalation methods
Service Packs
Service Packs combine previous patches including security fixes, performance improvements as well as support for new types of hardware. A newer Service Pack version incorporates previous Service Pack patches.
Kernel
The kernel contains a set of functions that provide fundamental mechanisms. It provides scheduling or synchronization, which is used by components and low-level hardware architecture. It is written in C and contains assembly code for complex tasks that require access to special registers. The kernel’s tasks include reading and writing to memory and communicating with input and network devices. [1]
Registry
The registry is a central component that contains necessary boot and system information, system-wide software settings, the security database and also per-user configuration settings.
| Root Key | Abbreviation | Description |
| HKEY_CURRENT_USER | HKCU | Stores data associated with the currently logged-on user. This root key is mapped to the currently logged user’s key in HKEY_USERS |
| HKEY_USERS | HKU | Stores information about all the accounts on the machine |
| HKEY_CLASSES_ROOT | HKCR |
Stores file association and Component Object Model (COM) object registration information |
| HKEY_LOCAL_MACHINE | HKLM | Stores system-related information and contains most keys |
| HKEY_PERFORMANCE_DATA | HKCC | Stores performance information |
| HKEY_CURRENT_CONFIG | HKPD | Stores some information about the current hardware profile |
The registry is composed of keys and values. A key is a container that can consist of keys and values. The highest level of keys is called root keys.
The registry can be accessed through Regedit.exe:
The registry contains the following six root keys [2]:
Processes
A process contains a set of resources used when executing the instance of the program [3]:
- a private virtual address space used to prevent a process to access or modify other processes’ or operating system data
- an executable program, which is mapped into the process’ private virtual address space
- a security context (called access token), which includes identification of the user, security groups, privileges, etc.
- a process ID
- one or more threads of execution
Jobs
A group of processes can be managed as a unit. The object that can control this group is called a job. Jobs are nameable and can be secured with certain security constraints. E.g. jobs can prevent processes from impersonating or creating processes with access tokens that contain the local administrator’s group. Furthermore, it is possible to enable the job to remove certain privileges and security IDs (SIDs) when threads are impersonated.
Services
Windows’ mechanism to start processes at system startup, which are not tied to an interactive user, are called Windows services. These are similar to UNIX daemon processes. An example of a user-independent process is a web server. This Windows service runs independently, regardless if a user is logged on or not.
For each service, a registry key exists in HKLM\SYSTEM\CurrentControlSet\Services.
The subkeys of a service’s key contain information regarding the executable file path, parameters and configuration options. If a service is configured to start from a particular account’s security context, the subkeys also contain the username.
Service Accounts
Services run in the context of user accounts. Unless otherwise specified, a service runs under the local system account (referred to as SYSTEM or LocalSystem), which possesses the highest privileges.
| Name | Privileges | Attributes |
| Local System Account | Can enable all privileges -> Highest privileges possible | Also called SYSTEM Windows components run under this account |
| Network Service Account | Some privileges including SeImpersonate | Used for services that authenticate to network services |
| Local Service Account | Same as Network Service Account but not for authenticating to network services |
Startup Programs
Startup programs (also called autoruns) are similar to services with the difference that services are managed by the Service Manager.
PRIVILEGE ESCALATION METHODS AND TECHNIQUES
Some important and effective local privilege escalation methods and techniques are described in this section. These have been ordered by their success rate.
Outdated Software
In a company environment, updates cannot always be deployed in a timely fashion. Compatibility, availability, resource problems, or a high number of systems are possible reasons for delayed or missing updates. This opens further vectors to escalate privileges.
The following graph depicts the possibilities to elevate privileges by exploiting outdated software:
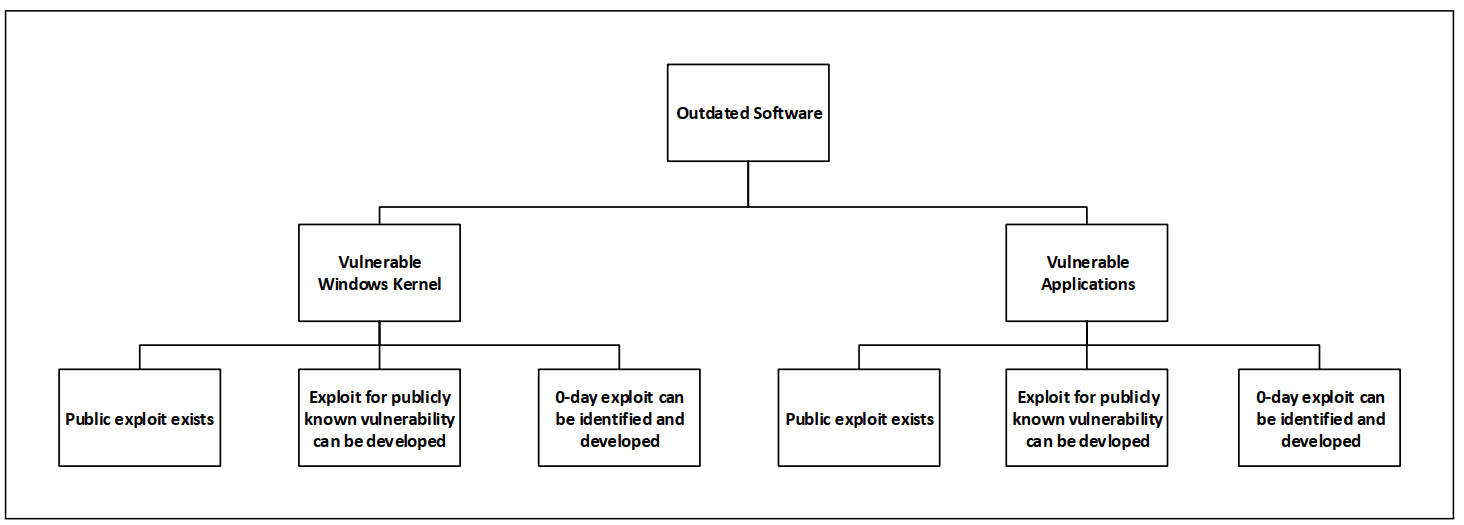
Windows Kernel
Vulnerabilities in
the Windows kernel are published from time to time of which many can be used to
escalate privileges.
The following command can be used to retrieve installed patches and their date:
wmic qfe get Caption,Description,HotFixID,InstalledOn
Hereafter, the HotFixID (KB*) can be compared to the HotFixIDs in Microsoft’s security bulletin database. A missing HotFixID on the system means that a patch is missing and potentially an exploit can be used to escalate privileges.
Vulnerable Applications
Most software contains thousands of lines of code written by multiple developers. Ensuring that no vulnerabilities creep in, is virtually impossible. If a vulnerability can be used to execute arbitrary code and that application runs under high privileges, a successful exploit leads to escalated privileges. For this method, the first step is to retrieve currently installed software and their versions. Publicly available exploits for these software versions can be searched by using Google or dedicated exploit databases. If no exploits are publicly available, one might, depending on the time resources, consider developing an exploit or finding a 0-day vulnerability.
Wmic can be used to retrieve installed software and their versions:
wmic product get name, version
Insecure Services
One possible way to escalate privileges is by exploiting misconfigured services. The goal is to embed a malicious file in a high privileged service. This file will then be executed the next time the service starts and will have the same privileges as the service possesses. As most services start with SYSTEM privileges, the chance to obtain SYSTEM privileges is high.
The following graph depicts the possibilities to elevate privileges by exploiting insecure services:
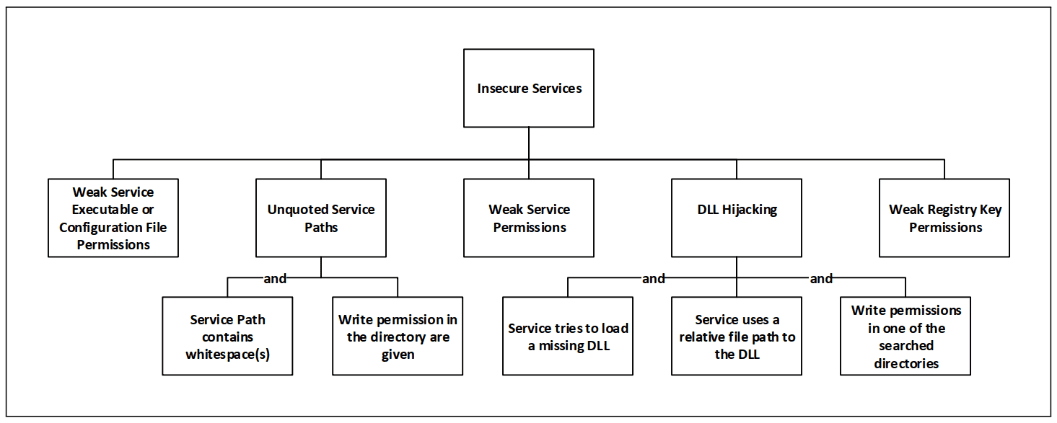
Weak Service Executable or Configuration File Permissions
Services execute the file defined in their file path. If this file can be modified by an attacker, he is able to replace it with a malicious file of his own.
Furthermore, services sometimes load configuration files. Depending on the program, it might be possible that such a configuration file can be used to execute an arbitrary file. If write permissions for such a configuration file exists, privileges can be escalated.
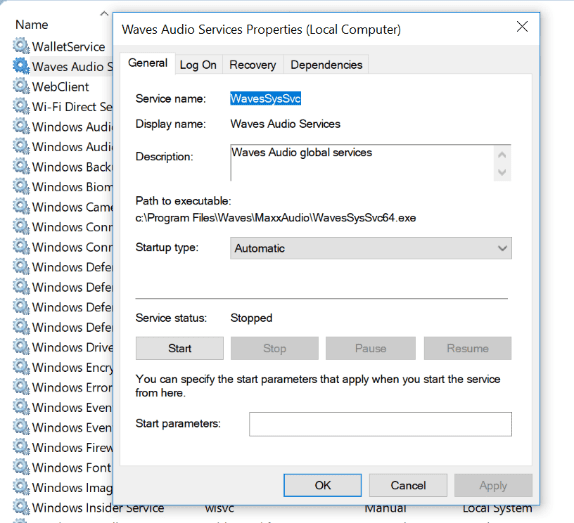
The following figure shows that the binary file of a service WavesSysSvc, which runs under SYSTEM privileges, can be modified by any one of the group Users as they possess write permissions (permissions were modified in this example for demonstration purposes):
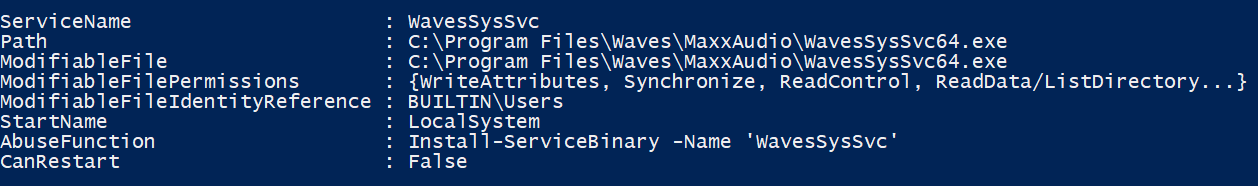
The output was generated with PowerSploit’s PowerUp script using the Get-ModifiableServiceFile method.
Weak Service Permissions
Weak service permissions can be used to modify the binary path in a service and hereby execute arbitrary files.
DLL Hijacking
Windows
applications usually load DLL files when started. It may happen that a DLL file
does not exist and the application is unable to load it. Nevertheless, an
application will continue to execute as long as the missing DLL is not needed.
In case the application uses a relative and not an absolute file path, Windows
searches for the file in the following directories:
- The directory from which the application is loaded
- C:\Windows\System32
- C:\Windows\System
- C:\Windows
- The current working directory
- Directories in the system PATH environment variable
- Directories in the user PATH environment variable
The folders C:\Windows and “C:\Program Files” are usually protected as no low
privileged users are able to write in these. Therefore, the highest potential
for a successful DLL hijack is given when a low privileged user has write
access to a directory included in the system or user PATH environment variable.
A low privileged user can place a malicious DLL file with the same name as the
missing DLL in one of these directories. When the application is started, this
DLL file is loaded and will run under the application’s privileges.
To search for missing DLLs, PowerSploit can be used with the following script:
Find-ProcessDLLHijack
Hereafter, we can check the permissions in the directories that Windows searches for DLL files:
Find-PathDLLHijack
In the last step we can create a malicious DLL file with the following script:
Write-HijackDll
If this is the case, we can move our malicious DLL file to the directory we have write access to. The next time the application is started, the created DLL file will be executed.
Unquoted Service Paths
Another way to escalate privileges is to exploit the order in which Windows searches for executables based on the value defined in the ImagePath parameter of a service when this value contains spaces and is not embedded within double-quotes. An example can be seen in the following figure for the WavesSysSvc service, a sound manager application that comes shipped with DELL laptops (to our knowledge this vulnerability was fixed):
Windows first tries to execute an executable file in the location where the first space is. E.g. the service path
C:\Program Files\Waves\MaxxAudio\WavesSysSvc64.exe
would lead Windows to first search for an executable file Program.exe in the C:\ directory:
C:\Program.exe
This applies to every space in the unquoted service path. If this file exists, Windows executes it. If it does not exist, the subsequent path is executed. An attacker that can write to the C:\ directory would be able to place an executable file named Program.exe in the directory. The next time the service starts, this file is executed.
Major vendors sometimes deploy software with unquoted service paths. E.g. in 2017 Lenovo patched an unquoted service path in the ElanTech Touchpad Driver, which is deployed on most of their notebooks. Also, Dell fixed unquoted service paths in one of their software called Dell Active Roles in 2017.
Please note, that this technique requires write permissions for low privileged users for a directory in the service path. Normally, a low-privileged user does not have write permissions to C:\. However, there is still the chance that write permissions exist for a directory in the remaining service path.
Insecure Credentials
Finding a clear-text password or guessing it may allow for authentication as another user.
The following graph depicts the possibilities to elevate privileges by attacking insecure credentials:
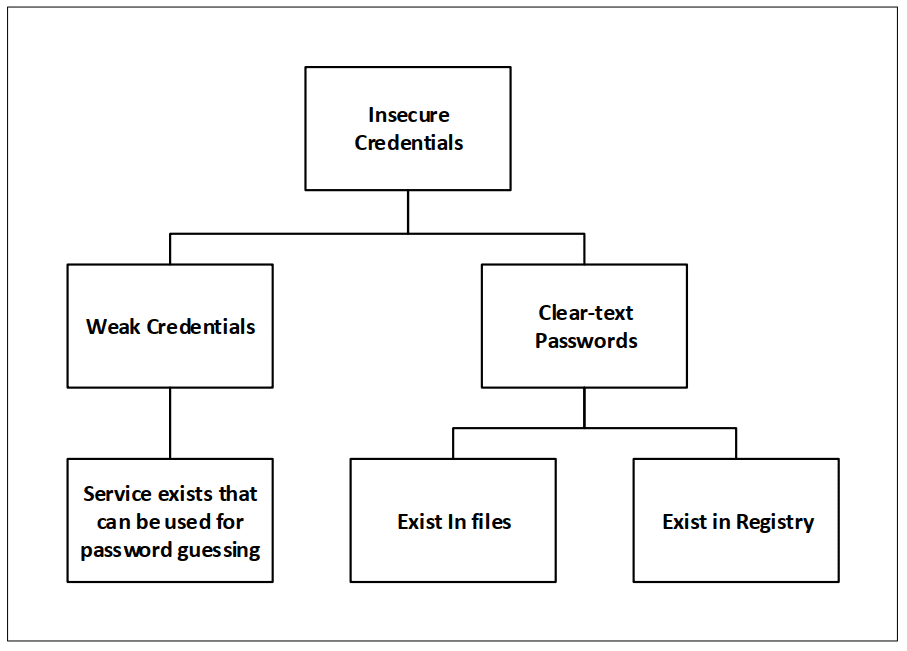
Clear-text Passwords
In the process of automating different tasks, system administrators often knowingly or unknowingly write clear-text passwords in files or in the registry of accounts, which are used for authenticating to different services.
One example is that when administrators want to deploy images on a large number of devices without user interaction (called unattended installations) they use the Windows Deployment Services. However, this requires that the local system administrator’s password or other, privileged account passwords are stored in one or more of the following locations:
- C:\unattend.xml
- C:\Windows\Panther\Unattend.xml
- C:\Windows\Panther\Unattend\Unattend.xml
- C:\Windows\system32\sysprep.inf
- C:\Windows\system32\sysprep\sysprep.xml
As an example, the following CMD commands can be used to search for passwords in configuration files:
findstr /si password password *.txt
findstr /si password password *.xml
findstr /si password password *.ini
findstr /si password password *.dat
Furthermore, the following PowerSploit scripts can be used:
Get-UnattendedInstallFile
Get-Webconfig
Get-ApplicationHost
Get-SiteListPassword
Get-CachedGPPPassword
The following commands are used to search for passwords in the registry:
reg query HKLM /f password /t REG_SZ /s
reg query HKLM /f password /t REG_SZ /s
reg query HKU /f password /t REG_SZ /s
reg query HKU /f password /t REG_SZ /s
reg query HKCU /f password /t REG_SZ /s
reg query HKCU /f password /t REG_SZ /s
Insufficient Physical Access Manipulation Protection
Further privilege
escalation attack vectors exist if physical access to the target system is
available. This section describes how privileges can be escalated on a system,
which an attacker has physical access to and which is protected insufficiently
against file manipulation.
The following graph depicts the possibilities to elevate privileges by
attacking devices which we have physical access to:
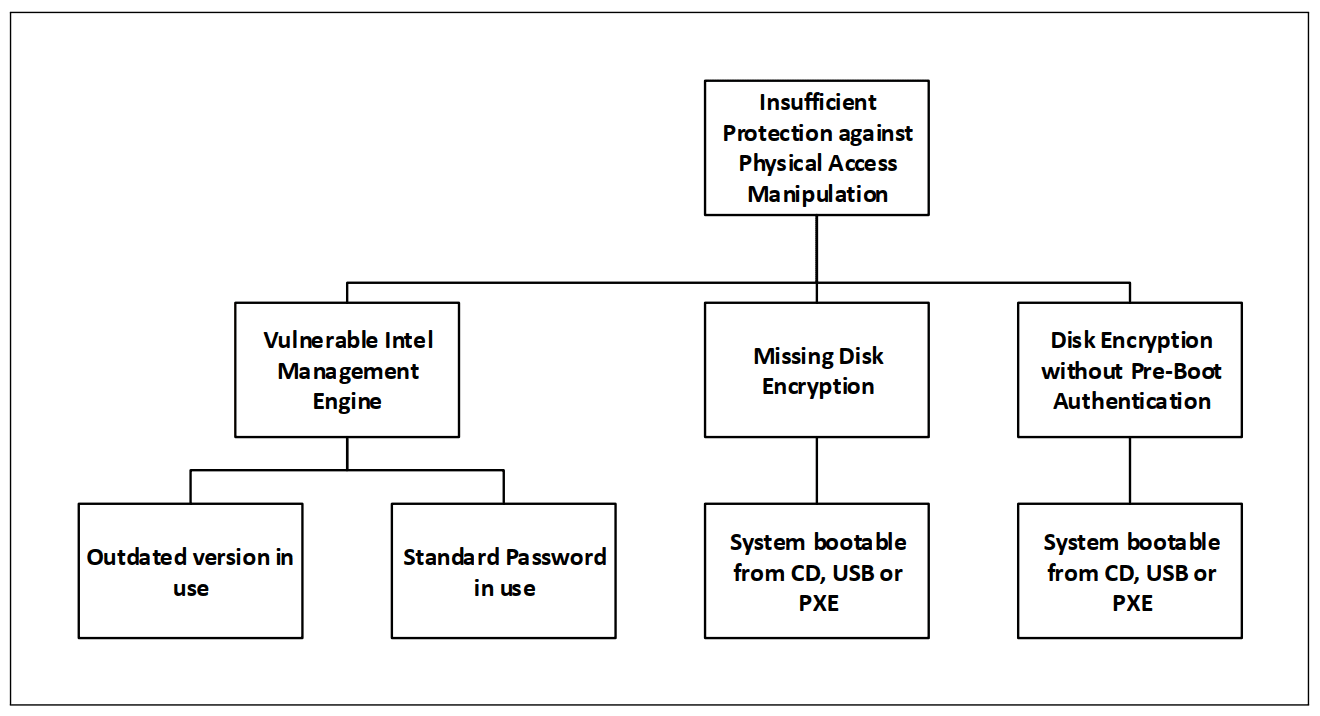
Missing Disk Encryption
A machine that does not encrypt the Windows partition and allows booting from CD, USB or a pre-boot execution environment (PXE) is prone to privilege escalation through file manipulation. Such a machine can be compromised by booting a live operating system and replacing an executable file that is executed within a Windows service running with SYSTEM privileges. One example is the utilman.exe file used for input assistance (Ease of Access) at the Windows logon screen. This file can be replaced by cmd.exe. The following figure shows that a CMD with SYSTEM privileges is opened when clicking on the Ease of Access button:
Disk Encryption without Pre-boot Authentication (Cold Boot Attack)
Disk encryption software may use pre-boot authentication to ensure that a file volume is decrypted after providing a password, smartcard, etc. A number of disk encryption software load the decryption key into the RAM. If an already decrypted machine is shut down and can be booted from CD, USB or a PXE, it is possible to dump the RAM data of that machine by booting software that dumps the RAM. This is possible as RAM, although it is a volatile storage, does not directly erase data when it is no longer supplied with power, but it is erased gradually. The time after which RAM data is deleted can be extended to several hours by cooling the RAM, e.g. by spraying nitrogen on the RAM. Such an attack is also referred to as Cold Boot attack.
Some companies choose not to use pre-boot authentication in order to enable a PXE or to improve user experience. Here, the key is loaded into memory when booted. These machines can be started and shut down several times. Therefore, the memory can be dumped repeatedly until it contains the decryption keys. This increases the chance of a successful key extraction. Such attacks have been demonstrated by the Princeton University research.
Thanks for visiting this blog!
For professional Windows penetration testing training visit https://certcube.com



Pretty! This was an extremely wonderful article.
Thank you for providing these details.
Thanks for the list