Wfuzz- The power of evil
WfFuzz is a web application brute forcer that can be considered an alternative to Burp Intruder as they both have some common features. It ́s a web application brute forcer, that allows you to perform complex brute force attacks in different web application parts as GET/POST parameters, cookies, forms, directories, files, HTTP headers authentication, forms, directories/files, headers files, etc. It has a complete set of features, payloads and encodings.
If we know part of the name of the web file, which is part of the web application, and it accepts the input argument id that is used by the application to locate the resource to be downloaded, usually, we would have to write a bash script similar to this one to do that:
#!/bin/bash for id in $(seq 1 10000); do echo "http://www.xyz.com/index.php?id=$id" done
Instead of the echo command, which just prints the URI on the screen, we would have to use a tool like wget or curl or something like that to actually download the resource, which can be analyzed later by VOKA. The script above is very simple, but why should we program such bash scripts if we have wfuzz. With wfuzz this is a simple matter of executing the following:
# wfuzz -v -z range,1-10000 http://www.xyz.com/index.php?id=FUZZ
The basic architecture of the Wfuzz Bruteforce program is as follows. It contains the elements listed below:
– payloads: the generated list of data to be sent to the web server.
– encoders: used to encode the payload in several ways, which is useful if the value in some parameter needs to be URL encoded, base64 encoded, or if the value should hold Unicode data, etc. There are also hash functions like md5 and sha1, which can also be used to generate the hash representation of the payload. A useful feature is a multiple encoding of the same payload, which can be great if some data is the first base64 encoded and then only the md5 hash is needed or something like that.
– iterators: used to iterate over all payloads. The iteration process can be done in several ways, but Wfuzz supports the three iterators: product, zip and chain. We need to remember that in our request URI we need to include the words FUZZ, FUZ2Z, FUZ3Z, …, FUZNZ, which will be replaced by the selected payloads in each iteration. The payload for each FUZZ element is selected by each –z option we’re passing the wfuzz command. We can also use the -V option to fuzz all variables in a request, in which case we don’t need the FUZZ keyword.
– plugins: used to extend the features of the wfuzz program.w
– printers: used to output the results in certain formats. Supported formats are the magic tree, HTML.
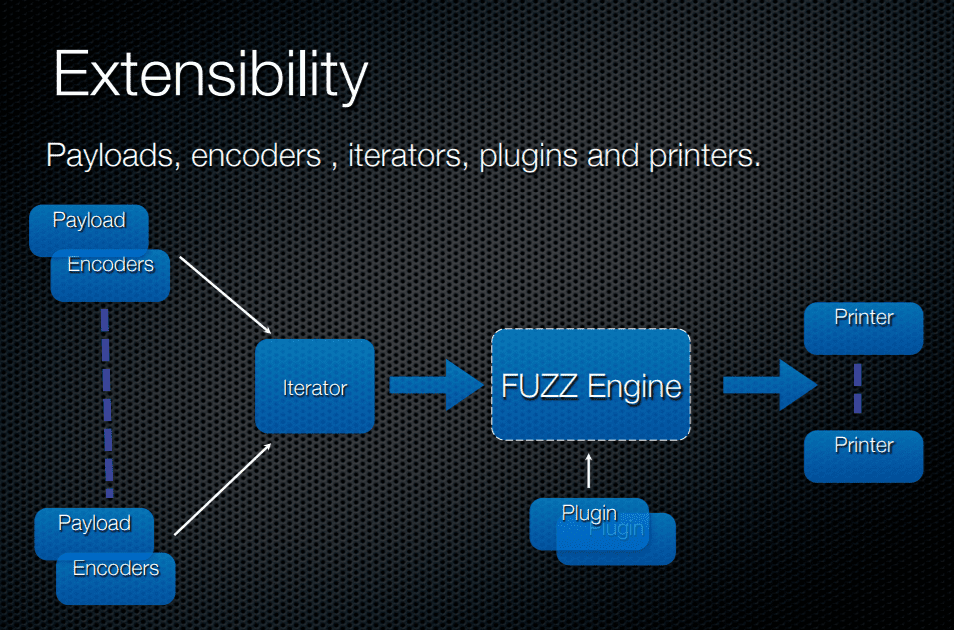
Payloads
We already mentioned that payloads are generated data to be sent to the target web site. There are different kinds of payloads, which are listed and explained below.
- file: read entries from a file: an example is file, wordlist/general/commons.txt, which specifies all the entries that are contained in the chosen file.
- stdin: read entries from standard input
- list: generate entries from a list of objects: an example is a list,a-b-c, which specifies the three entries, the letters ‘a’, ‘b’ and ‘c’.
- hexrand: generate hexadecimal random objects
- range: generate a range of numbers: an example is a range,0-2, which specifies the three entries, the numbers 0,1,2.
- names: generates all possible combinations used in account naming patterns.
- hexrange: generate hexadecimal random objects
- permutation: performs a permutation of the given parameter
- All available payloads can be printed with “wfuzz -e payloads”:
An example command that chooses to fuzz the parameter ‘d’ in the index.php is shown below # wfuzz --hc 403 -c -z range,0-2 <a href="https://www.xyz.com/index.php?d=FUZZ">https://www.xyz.com/index.php?d=FUZZ</a>
2.2. Encoders
Encoders are used to encode the payloads in several ways. The -z option in Wfuzz specifies the payload and its corresponding encoder in format (type, parameters, encoding).
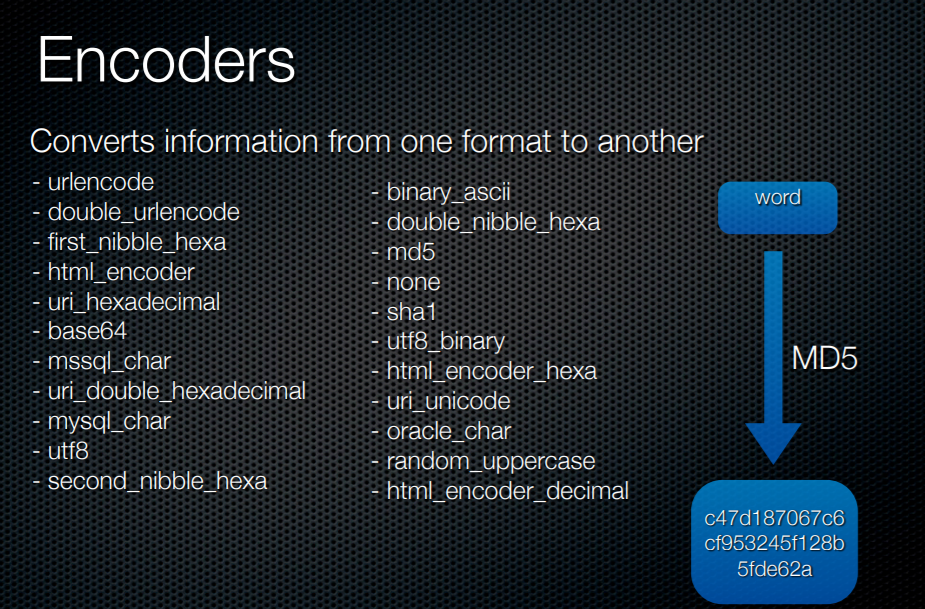
# wfuzz -e encodings
To use an encoder, we need to specify the third option to the -z argument. The following example fuzzes the md5 argument, which accepts the md5 of the user’s password. We’re using the file passwords.txt as a payload, where the md5 of each password (a password is specified in its own line) is computed and fed into the md5 parameter.
# wfuzz -c -z list,passwords.txt,md5 <a href="https://www.xyz.com/index.php?d=FUZZ">https://www.xyz.com/index.php?md5=FUZZ</a>
Iterators
Iterators support three methods that can be used to iterate over payloads and are described in detail below:
- product (default): combines the first and second payload lists to construct all possible combinations.
- zip: takes the first value from the first payload list and combines it with a corresponding value in the second payload list.
- chain: combines the first and second payload list to make a new bigger payload list.
Iterators
Iterators support three methods that can be used to iterate over payloads and are described in detail below:
- product (default): combines the first and second payload list to construct all possible combinations.
- zip: takes the first value from the first payload list and combines it with a corresponding value in the second payload list.
- chain: combines the first and second payload list to make a new bigger payload list.
Usage
below is shown an example of fuzz looking for common directories:
$ wfuzz -w wordlist/general/common.txt http://testphp.vulnweb.com/FUZZ
Below is shown an example of wfuzz looking for common files:
$ wfuzz -w wordlist/general/common.txt http://testphp.vulnweb.com/FUZZ.php
Password cracking
- Vertical scanning (different password for each user)
- Horizontal scanning (different usernames for common passwords) Diagonal scanning (different username/password each round)
- Three dimensions (Horizontal, Vertical or Diagonal + Distributing source IP)
- Four Dimensions (Horizontal, Vertical or Diagonal + Time Delay + Distributing Source IP)
Password cracking
- Diagonal — admin/test • guest/guest • user/1234x
- Horizontal — admin/test guest/test user/test
Password cracking Horizontal
wfuzz –z list,pass1-pass –z list,us1-us2 http:// target.com/user=FUZ2Z &pass=FUZZ
Password cracking Three dimensional
wfuzz –z list,pass1-pass –z list,us1-us2 –s 1 http:// target.com/user=FUZ2Z &pass=FUZZ
Password cracking Four-dimensional
wfuzz –z list,pass1-pass –z list,us1-us2 –s 1 –p ip:8080- ip2:8080-ip3:8088 http://target.com/user=FUZ2Z &pass=FUZZ
wfuzz –z list,user1-user2 –z list,pass1-pass2 <a href="http://target.com/username=FUZZ&password=FUZ2Z">http://target.com/username=FUZZ&password=FUZ2Z</a>
Permutation payload
wfuzz -c -z permutation,abcdefghijk-2 -z permutation, 1234567890-2 --hc 404 --hl BBB http://localhost:8888/test/ parameter.php? action=FUZZ{a}FUZ2Z{a}
Fuzzing Parameters In URLs
You often want to fuzz some sort of data in the URL’s query string, this can be achieved by specifying the FUZZ keyword in the URL after a question mark:
$ wfuzz -z range,0-10 --hl 97 http://testphp.vulnweb.com/listproducts.php?cat=FUZZ
# URL brute forcing
wfuzz -c -z file,Directories_Common.wordlist --hc 404 http://<host>/FUZZ.php#
Fuzzing Requests
GET params brute forcing
wfuzz -c -z file,users.txt -z file,pass.txt --hc 404 http://<host>/index.php?user=FUZZ&pass=FUZ2
If you want to fuzz some form-encoded data like an HTML form will do, simply pass a -d command-line argument:
POST params brute forcing
$ wfuzz -z file,wordlist/others/common_pass.txt -d "uname=FUZZ&pass=FUZZ" --hc 302 http://testphp.vulnweb.com/userinfo.php
Fuzzing Cookies
To send your own cookies to the server, for example, to associate a request to HTTP sessions, you can use the -b parameter (repeat for various cookies):
$ wfuzz -z file,wordlist/general/common.txt -b cookie=value1 -b cookie2=value2 http://testphp.vulnweb.com/FUZZ
The command above will generate HTTP requests such as the one below:
GET /attach HTTP/1.1 Host: testphp.vulnweb.com Accept: */* Content-Type: application/x-www-form-urlencoded Cookie: cookie=value1; cookie2=value2 User-Agent: Wfuzz/2.2 Connection: close
Cookies can also be fuzzed:
$ wfuzz -z file,wordlist/general/common.txt -b cookie=FUZZ http://testphp.vulnweb.com/
Fuzzing Custom headers
If you’d like to add HTTP headers to a request, simply use the -H parameter (repeat for various headers):
$ wfuzz -z file,wordlist/general/common.txt -H "myheader: headervalue" -H "myheader2: headervalue2" http://testphp.vulnweb.com/FUZZ
The command above will generate HTTP requests such as the one below:
GET /agent HTTP/1.1 Host: testphp.vulnweb.com Accept: */* Myheader2: headervalue2 Myheader: headervalue Content-Type: application/x-www-form-urlencoded User-Agent: Wfuzz/2.2 Connection: close
You can modify existing headers, for example, for specifying a custom user agent, execute the following:
$ wfuzz -z file,wordlist/general/common.txt -H "myheader: headervalue" -H "User-Agent: Googlebot-News" http://testphp.vulnweb.com/FUZZ
The command above will generate HTTP requests such as the one below:
GET /asp HTTP/1.1 Host: testphp.vulnweb.com Accept: */* Myheader: headervalue Content-Type: application/x-www-form-urlencoded User-Agent: Googlebot-News Connection: close
Headers can also be fuzzed:
$ wfuzz -z file,wordlist/general/common.txt -H "User-Agent: FUZZ" http://testphp.vulnweb.com/
Fuzzing HTTP Verbs
HTTP verbs fuzzing can be specified using the -X switch:
$ wfuzz -z list,GET-HEAD-POST-TRACE-OPTIONS -X FUZZ http://testphp.vulnweb.com/
If you want to perform the requests using a specific verb you can also use “-X HEAD”.
Proxies
If you need to use a proxy, simply use the -p parameter:
$ wfuzz -z file,wordlist/general/common.txt -p localhost:8080 http://testphp.vulnweb.com/FUZZ
In addition to basic HTTP proxies, Wfuzz also supports proxies using the SOCKS4 and SOCKS5 protocol:
$ wfuzz -z file,wordlist/general/common.txt -p localhost:2222:SOCKS5 http://testphp.vulnweb.com/FUZZ
Multiple proxies can be used simultaneously by supplying various -p parameters:
$ wfuzz -z file,wordlist/general/common.txt -p localhost:8080 -p localhost:9090 http://testphp.vulnweb.com/FUZZ
Each request will be performed using a different proxy each time.
Authentication
Wfuzz can set authentication headers by using the –basic/NTLM/digest command-line switches.
For example, a protected resource using Basic authentication can be fuzzed using the following command:
$ wfuzz -z list,nonvalid-httpwatch --basic FUZZ:FUZZ https://www.httpwatch.com/httpgallery/authentication/authenticatedimage/default.aspx
If you want to fuzz a resource from a protected website you can also use “–basic user: pass”.
Recursion
The -R switch can be used to specify a payload recursion’s depth. For example, if you want to search for existing directories and then fuzz within these directories again using the same payload you can use the following command:
$ wfuzz -z list,"admin-CVS-cgi\-bin" -R1 http://testphp.vulnweb.com/FUZZ
Performance
Several options let you fine-tune the HTTP request engine, depending on the performance impact on the application, and on your own processing power and bandwidth.
You can increase or decrease the number of simultaneous requests to make your attack proceed faster or slower by using the -t switch.
You can tell Wfuzz to stop a given number of seconds before performing another request using the -s parameter.
Writing to a file
Wfuzz supports writing the results to a file in a different format. This is performed by plugins called “printers”. The available printers can be listed executing:
$ wfuzz -e printers
For example, to write results to an output file in JSON format use the following command:
$ wfuzz -f /tmp/outfile,json -w wordlist/general/common.txt http://testphp.vulnweb.com/FUZZ
Different output
Wfuzz supports showing the results in various formats. This is performed by plugins called “printers”. The available printers can be listed executing:
$ wfuzz -e printers
For example, to show results in JSON format use the following command:
$ wfuzz -o json -w wordlist/general/common.txt http://testphp.vulnweb.com/FUZZ
When using the default output you can also select an additional FuzzResult’s field to show together with the payload description:
$ wfuzz -z range --zD 0-1 -u http://testphp.vulnweb.com/artists.php?artist=FUZZ --field r
The above is useful, for example, to debug what exact HTTP request Wfuzz sent to the remote Web server. Check the filter language section in the advance usage document for the available fields.
References


Recent Comments