Searchsploit Cheat Sheet
Searchsploit an exploit search tool by Offensive Security, Unix Ninja & G0tmi1k. It allows you to take a copy of Exploit Database with you. SearchSploit gives you the power to perform detailed off-line searches through your locally checked-out copy of the repository. This capability is particularly useful for security assessments on segregated or air-gapped networks without Internet access.
Installation Kali Linux / Linux
If you are using the standard GNOME build of Kali Linux, the “exploit-DB” package is already included by default! However, if you are using the Kali Light variant or your own custom-built ISO, you can install the package manually as follows:
root@kali:~# apt update && apt -y install exploitdb You may wish to install some other related packages, “exploit-DB-papers” and “exploit-DB-bin-sploits”.
Installation Apple OS X/macOS
If you have homebrew (package, formula) installed, running the following will get you set up:
user@MacBook:~$ brew update && brew install exploitdbAlternatively, if you do not have brew installed, you can install it with Git
Updating SearchSploit
If you are using Kali Linux, you can expect the exploit-DB package to be updated weekly. If you are using Homebrew or Git, you can expect daily updates (at 05:05 UTC).
Regardless of how you installed SearchSploit, all you need to do in order to update it is run the following:
$ searchsploit -uIf you are using the Kali Linux package and haven’t updated since before 20 September 2016 (shame on you), you will first need to update the package in the traditional manner:
root@kali:~# apt update && apt -y full-upgradePlease note, we do not recommend you use GitHub’s .zip or the legacy archive.tar.bz2 packages to update.
Using SearchSploit
Help Screen
By using -h, you can see all the features and options that are available to you:

Basic Search
Simply add any number of search terms you wish to look for:

Note, SearchSploit uses an AND operator, not an OR operator. The more terms that are used, the more the results will be filtered out.
Pro Tip: Do not use abbreviations (use SQL Injection, not SQLi).
Pro Tip: If you are not receiving the expected results, try searching more broadly by using more general terms (use Kernel 2.6 or Kernel 2.x, not Kernel 2.6.25).
Title Searching
By default, searchsploit will check BOTH the title of the exploit as well as the path. Depending on the search criteria, this may bring up false positives (especially when searching for terms that match platforms and version numbers). Searches can be restricted to the titles by using the -t option:

Removing Unwanted Results
you can remove unwanted results by using the --exclude option. We are also able to remove multiple terms by separating the value with a | (pipe). This can be demonstrated by the following:

Pro Tip: By doing: searchsploit linux kernel --exclude="(PoC)|/dos/" | grep ' 3.2', you’ll get even “cleaner” output (sorted based on the version without any heading/footers).
Piping Output (Alternative Method of Removing Unwanted Results)
The output from searchsploit can be piped into any other program, which is especially useful when outputting the results in JSON format (using the -j option). With this, it is possible to remove any unwanted exploits by using grep. In the following example, we use grep to filter out any “Denial of Service (DoS)” results.

Pro Tip: We recommend using “/poc/” with grep rather than “poc” so the filter is applied to the path, rather than the title.
Copy To Clipboard
So now that we have found the exploit we are looking for, there are various ways to access it quickly.
By using -p, we are able to get some more information about the exploit, as well as copy the complete path to the exploit onto the clipboard:
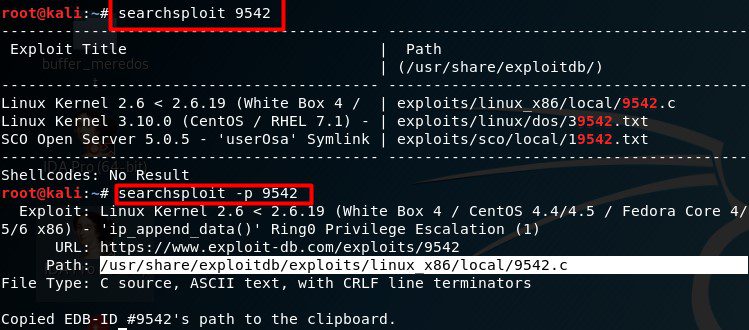
Copy To Folder
I recommend that you do not alter the exploits in your local copy of the database. Instead, make a copy of ones that are of interest and use them from a working directory. By using the -m option, we are able to select as many exploits we like to be copied into the same folder that we are currently in:

Exploit-DB Online
The Exploit Database repository is the main core of Exploit-DB, making SearchSploit efficient and easy to use. However, some of the exploit metadata (such as screenshots, setup files, tags, and vulnerability mappings) are not included. To access them, you will need to check the website.
You can quickly generate the links to exploits of interest by using the -w option:

Examining Nmap result
Nmap has a feature that let you save its output result in .xml format and we can identify each exploit associated with the Nmap XML file.
Nmap -Pn -n IP -oX output.xmlWith the help of above command, we have saved the scanning result of Nmap in an XML file, so that we can search the exploit related to scanned port/services.
searchsploit -x --nmap output.xmlExamine an Exploit
Using —examine option enables examine parameter to read the functionality of that exploit with the help of $PAGER.
searchsploit 9542 --examine

1 Response
[…] The following exploits are known to work well, search for another exploit using https://blog.certcube.com/searchsploit-cheat-sheet/ […]