OSCP – Detail Guide to Stack-based buffer Overflow – 3
Memory is the most crucial part of a system. We discussed memory and its working so now let’s see Memory in more details
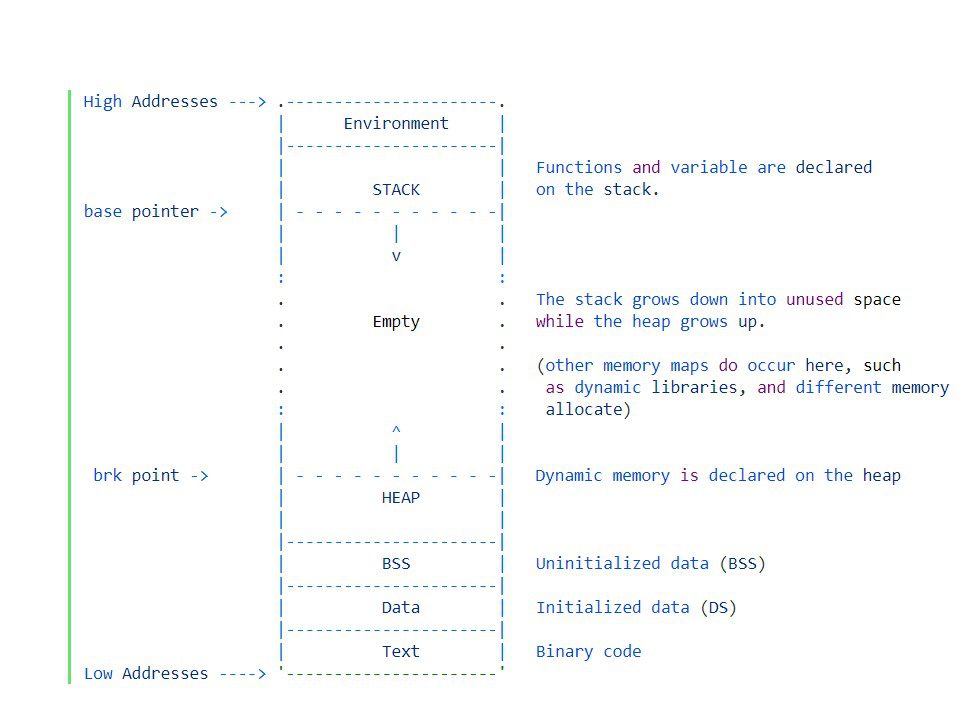
Generally, a process is laid out like it is defined in the figure .all above varios segments we have in program memory. So let’s get some idea about these segments
.text Segment: – The first segment is the actual program code in the .text segment where all the executable instructions are there
.data Segment:– Any data which has been inintilized to a value is stored
.bss Segment:– All uninitilized data store in .bss
Heap : – heap is used to generate dynamic memory whenever is required. In C we use malloc() function to use the dynamic memory. In c++ we use new and delete variable for the heap
We have a lot of unused memory
Stack: – The stack always points on top of the segment. we use the stack for storing arguments which are passed in the function as well as the local variables. The stack is also working as High to Low. Don’t worry at this time if you don’t understand about the stack as of now.
let’s discuss stack in more details coz its a very much important factor for BOF
Stack & It’s Working
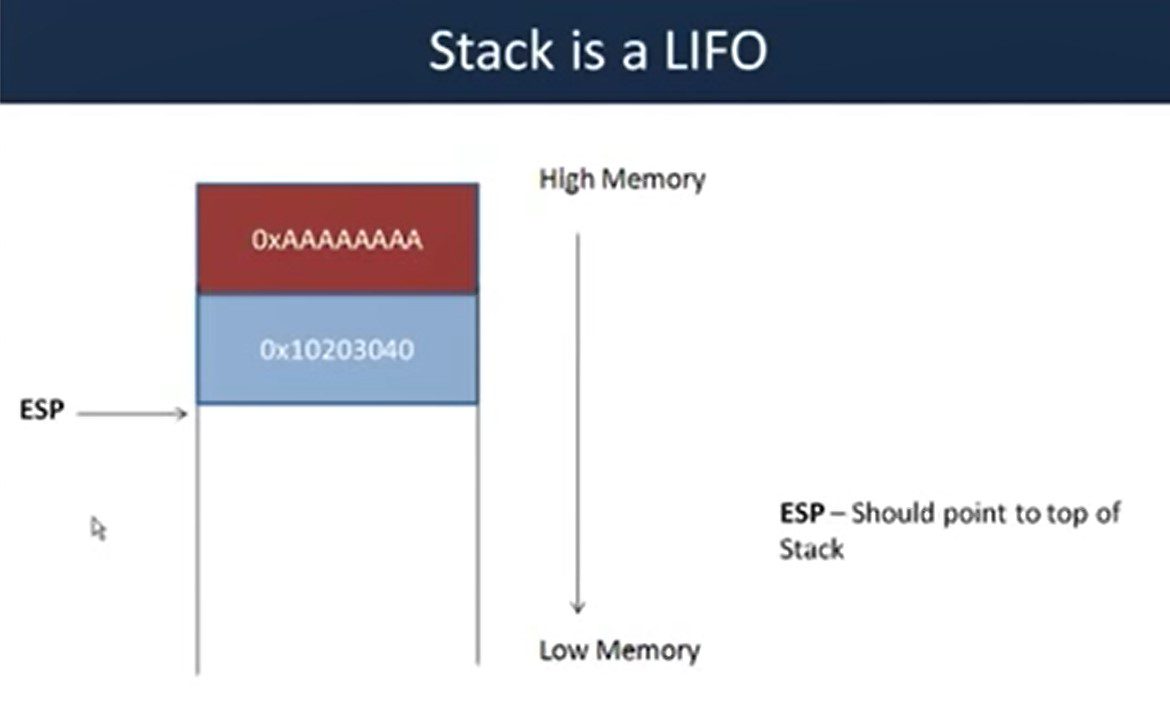
The stack is a last in first out data structure. As we already know it is working as high to low . Stack grows down to the memory. The ESP should be pointing out top of the stack.
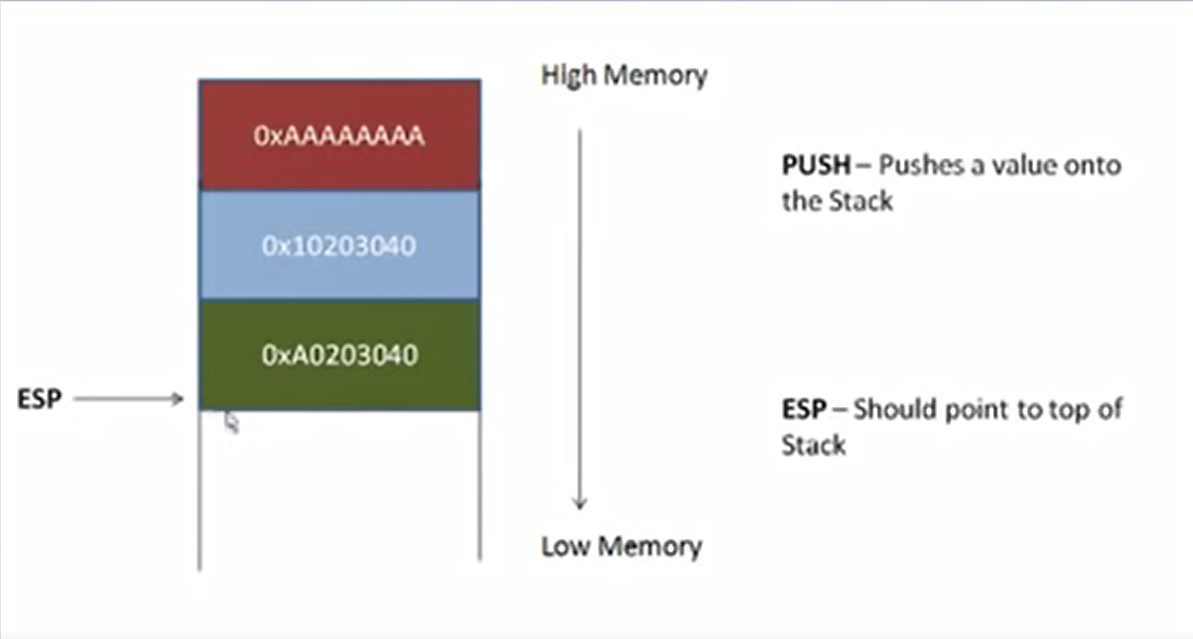
Stack support two operations: –
Push operation:– Push operation is used to pushing data into the stack. As soon as we push a value (2xA0203040) what one needs to do is update the stack pointer so now ESP will point the top of the stack after the adding the new value.
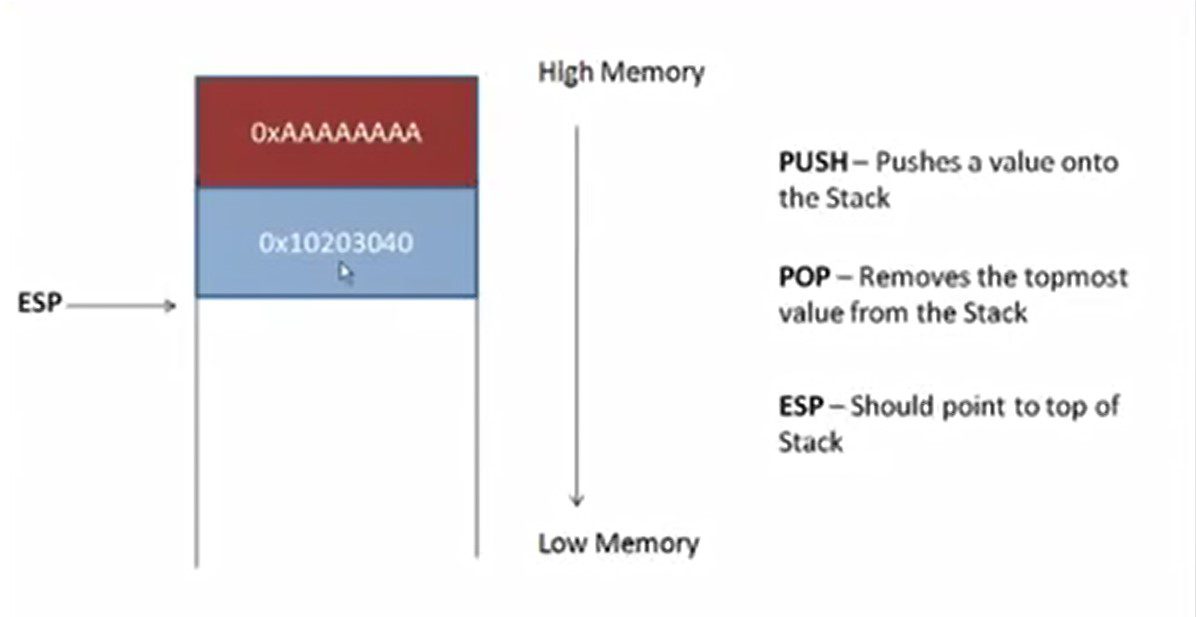
POP Operation: – Once you are done with using the value you used pop operation free the memory from the stack and again we subtract value from ESP and again Put ESP as the top of the stack
That’s all about this blog. We will discuss more stack and its operation in the next blog because it plays main role in the stack buffer overflow attack.
If you want to understand more deep information about stack and heap then visit this link
Thanks for visiting this blog. Join Certcube Labs for IT security Training & Certifications.
References : –


Recent Comments