OSCP – Detail Guide to Stack-based buffer Overflow – 4
So let’s look into the stack in more details we as we already know now how the stack is working.
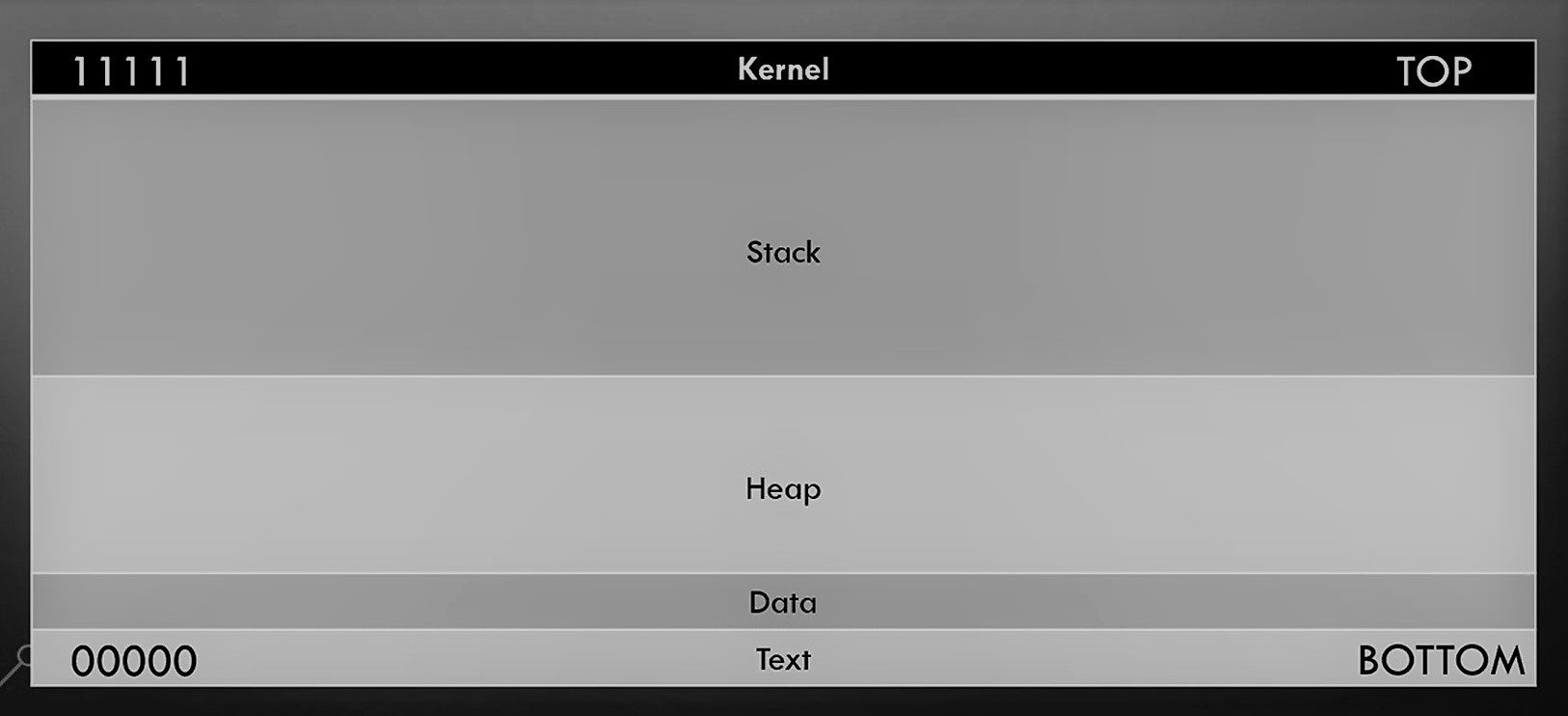
So now let’s get some more details about stack on the behalf of Registers.
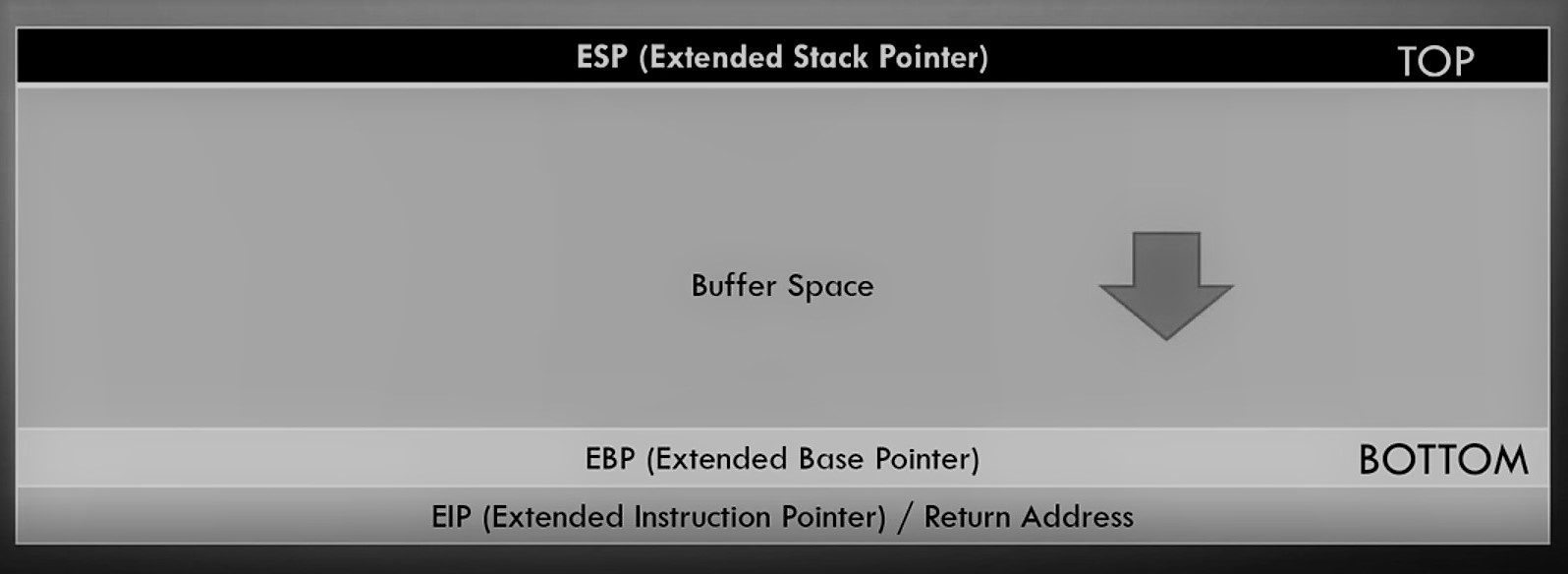
As we already discussed ESP, EBP, EIP in our second blog so you can check out the blog again. I am just pointing out some of the key points of the stack again : –
ESP sitting at the top and EBP is sitting at the bottom. In the middle, you have a buffer where you input some values. If you properly sanitize buffer space properly then it takes values and fill inside in it and stop at EBP.
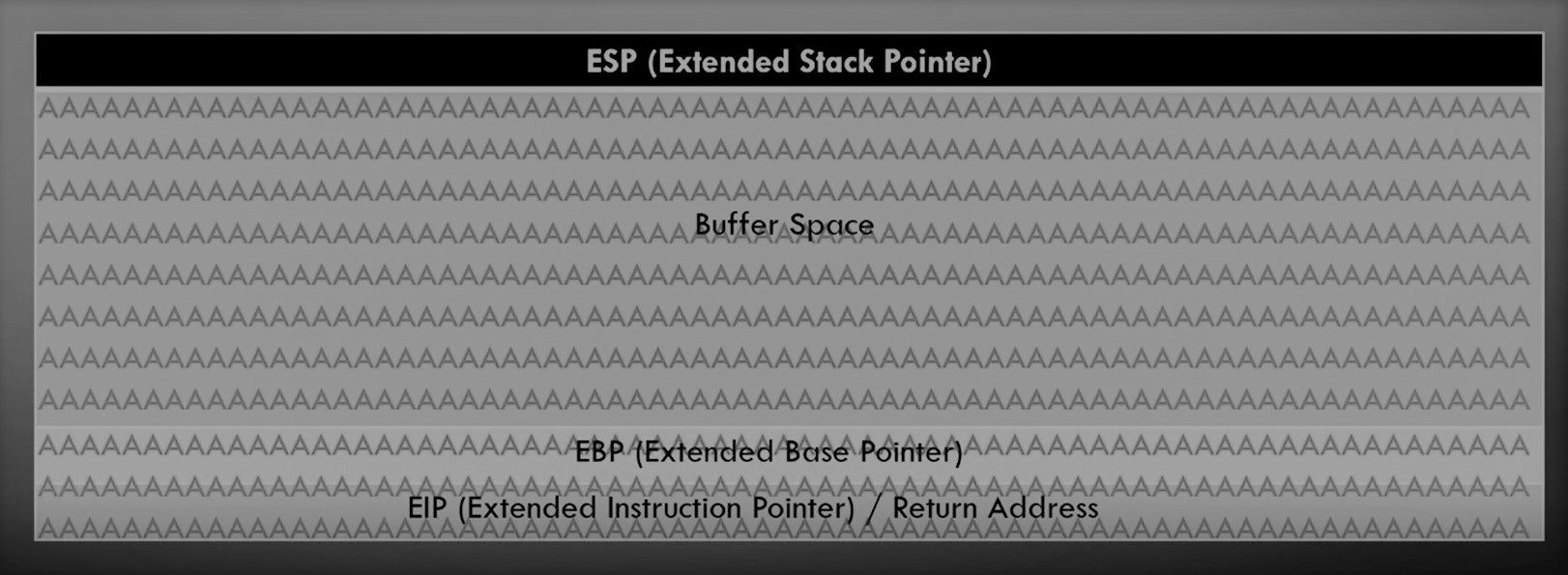
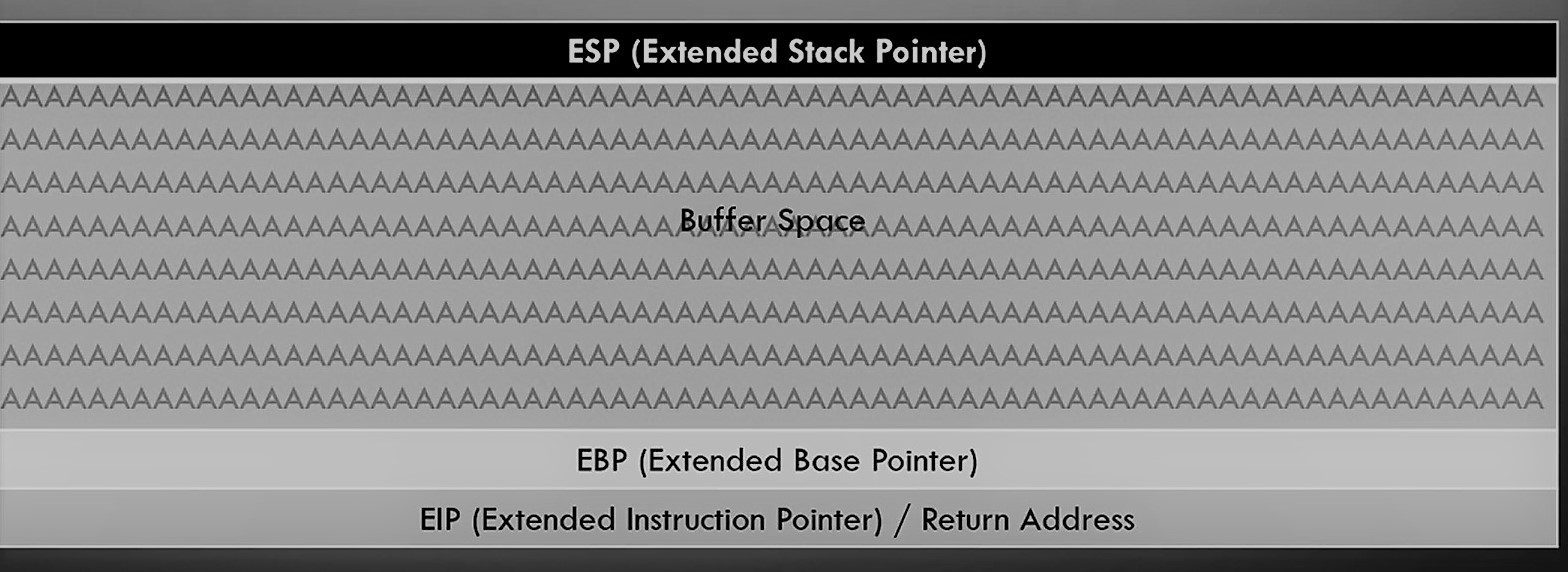
If this vulnerable for a buffer overflow attack then it will overflow the buffer space then EBP and EIP. the EIP is interesting coz it indicates the pointer address or return address. We can use this address to points the instructions and gain the reverse shell !!
Additionally, let’s check out some more details with a C program : –
Buffer Space
So what’s a buffer Space? Simply a buffer is a memory place or location which is used by a running program. This memory location is used to store some temporary data that is being used by the program. So for example, if we have a simple program that asks the user to enter his name and stores it in a variable called username then it prints “Hello username “. For example, if we run the program and enter the username as “cert”. The word “cert” is stored in the buffer until the program executes the print command and it retrieves the given username “cert” from the buffer to output the result: “Hello cert”
Our example written in c will be like this
#include <stdio.h>
int main () {
char username[20];
printf("Enter your name: ");
scanf("%s", username);
printf("Hello %s\n", username);
printf("Program exited normally");
return(0);
}
Break Down : int main() This defines the main function char username[20] This is where we specify the variable name but the most important thing about this line is char .... [20] this is where we specify the buffer for that variable, and I assigned it as 20 chars
The rest of the code takes the user input then prints it.
printf("Enter your name: "); scanf("%s", username); printf("Hello %s\n, username");
Now the program should ask us for username then print “Hello username” then print “program exited normally” and exits. The buffer for holding the username value is set to 20 chars, it’s good as long as the username length is less than 20 chars. But if the entered data is more than 20 chars length the program will crash because some data will be overwritten outside the buffer causing some parts of the program to be corrupted. So this condition called a buffer overflow condition.
That’s all about this blog. In Our Next blog, we will discuss how practically we will perform a buffer overflow attack.
Thanks for visiting this blog. Join Certcube Labs for IT security Training & Certifications.
References : –



Recent Comments